Hacker review of Cyberpunk (short story, 1980)
Welcome to the August issue of Hacker Chronicles!
I've got a treat for you cyberpunk lovers out there – a hacker review of the 1980 short story that started it, aptly named Cyberpunk.
Enjoy!
/John
Writing Update
Audiobook Publishing
Yay, two weeks later and Identified is now available as audiobook is more places. Enjoy Kristin Price's excellent narration through one of these links:
- Audible
- Apple Books
- Spotify, unclear if it works
- Audiobooks
- Storytel, Sweden
If you use another audiobook service, it's quite possible the book is available there too because I publish as widely as I can. And please email me links where you find it, or any weirdness in accessing it. The one service I know of that I haven't found a way to publish on is Bookbeat.
Soon Time for Beta Read of the Sequel Submerged!
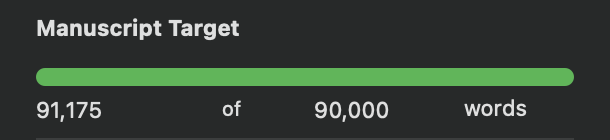
I've made a lot of progress on my revision of Submerged which is the sequel to Identified. All major changes are made and I'm down to just four mid-sized ones and twenty-six small ones.
At this point, I'm back above my target of 90k words.
Do you want to be a beta reader?
I have a couple of spots open, so if you can commit to max four weeks to read and provide feedback on the beta, let me know! The beta will be distributed as an ebook in the latter half of August (current estimate). Beta readers get a thank you in the book (if they wish).
August Feature: A Hacker Review of the Short Story Cyberpunk
Bruce Bethke wrote a short story titled Cyberpunk in 1980. He sold it for publication in 1982 and it appeared in the Amazing Stories magazine in 1983. It's available for free here: http://infinityplus.co.uk/stories/cpunk.htm. Go read it before you read my review – it's not long.
Bruce's title for his short story was the invention of a now well-known word and genre cyberpunk. In my view, the most seminal cyberpunk works out there are Ridley Scott's movie Bladerunner from 1982 (my review here), William Gibson's debut novel Neuromancer from 1984, and Neal Stephenson's Snow Crash from 1992.
So where did he come up with the word?
Four years earlier, 1976, the punk rock revolution had began in Britain. 1977 The Sex Pistols released "God Save the Queen" and at the end of 1979 The Clash released "London Calling." So punk culture was top of mind when he wrote his piece.

In parallel, 1975 the legendary Homebrew Computer Club had been formed and the subsequent years saw the rise of home computers and hacking beyond Phreaking, or phone hacking. I wrote extensively about this era in my February issue The Secret History of Hacking.
So in 1980 Bruce smushed together cyber (from cybernetics) and punk to capture his vision of computer punks, and wrote this now classic short story of what life could be like for such hackers.

Bruce Bethke himself, by a Cray supercomputer which what his daytime job is about.
Hacker Rating
Hacker Realism: ⭐️ ⭐️ ⭐️ ⭐️
Hacker Importance for the Plot: ⭐️ ⭐️ ⭐️ ⭐️ ⭐️
Hacks: ⭐️ ⭐️ ⭐️ ⭐️
Now let's get into the story, shall we?

At Buddy's All-Night Burgers
Mikey, the main character, gets a cryptic message on his terminal, or term as he calls it.
CRACKERS/BUDDYBOO/8ER
It's from his pal Rayno and it means someone has gotten access to the team's online data.
Worried that someone is following him, he takes public transportation the wrong direction and then back, plus a few transfers. Eventually he ends up at their favorite spot, Buddy's All-Night Burgers. Rayno is already there.
Lisa shows up but Georgie is late. Rayno starts telling them what's happened.
"The compiler's been cracked," he said. Lisa and I both swore. We'd worked up our own little code to keep our Net private. I mean, our Olders would just blow boards if they ever found out what we were really up to. And now somebody'd broken our code.
"Georgie's old man?" I asked.
"Looks that way."
Eventually Georgie shows up and they question him about his dad's hack into their data.
Georgie swears he's not leaked to his father. But he was asked questions this morning and that's why he's late.
Rayno says they got lucky because he spotted the intruder last night and made some changes to get the adversary off track.
Thoughts:
For being 1980 it is surprisingly modern with the team sharing online data and computation resources. But Bethke is of course envisioning the future.
It's unclear why a compiler is central and has been cracked. It could be that they use a custom-made compiler to obfuscate their malware. The goal of obfuscation is to scramble code to either make its digital fingerprint unique or make reverse engineering harder, or both. You can think of obfuscation as deliberate mutation of a biological virus to both circumvent immune systems that are trained on earlier versions of the virus and make it hard for biologists to analyze and understand the virus.
Hacking Session
Rayno gets out his "microterm" – a mobile computing devices that has terminal access to their network resources.
… there wasn't a system in CityNet it couldn't talk to.
The first hack Rayno shows off is ordering a "smartcab" – a taxi to take them where they want to go instead of using public transportation. They go to the library because it's deserted.
The library has terminals that move around which means the building has network outlets in many places. The team finds an unused one and Rayno connects his microterm.
Mikey gets them onto CityNet and they decide to hack for fun. Lisa goes first and gets back to a teacher who gave her an F. She charges him for hundreds of overdue library books and prints Encyclopedia Britannica in his office.
Mikey then gets them into an airline reservation system and starts cancelling flights.
Rayno says it's time for The Big One. They have been working on this hack for two months. Three weeks ago, Mikey finally got into Merchant's Bank & Trust and his access has been laying dormant since.
Rayno has decided they should use Mikey's bank access to steal money. He routes $50k through a few accounts and finally lands it on twenty dummy accounts.
Thoughts:
This is an odyssey of prankster-style hacking of the time. You mess with people's lives, you get good grades, and you steal money from the wealthy banks. You see this both in the movie WarGames from 1983 (my review here) and the movie Hackers from 1995 (my review here).
The microterm is a minimal, portable computer to connect to the network. It makes me think of netbooks from the late 2000s. Remember those?
Wikipedia: "A netbook is a small and inexpensive laptop designed primarily as a means of accessing the Internet."

Using a public library as their access point is prudent as long as they are not seen or captured on camera. Any investigation of the hacks would be traced back there.
Getting access to systems and then keeping the access points alive while not using them is classic. It is also a scary part of real hacking where deploying defenses today may not help you since your adversaries may have gotten in years ago and just maintain that access until the day they need it.
Rayno's split-up money transfer sounds akin to so called salami slicing but would need to be smaller per slice and performed over a longer period of time to truly be a slicing attack.
The Zeilemann Starfire 600
The team heads to a computer store called Martin's Micros.
The store owner Martin has a side gig writing software for real estate and he's hit a bug he can't figure out.
Mikey takes over and fixes the bug, and a few other bugs along the way. Martin is utterly impressed.
The team raves over a new computer that's just arrived in the store – a Zeilemann Starfire 600. Rayno says his model 300 is still faster but that's with thousands of dollars of modifications.
Mikey tries out the Starfire and wants it so badly he starts asking Martin for some kind of deal. The store owner suggests helping him with seven more software projects and he can have the 600.
Rayno cuts in and buys the Zeilemann Starfire 600 straight up, no haggling. When they get out of the store, Rayno gives the new computer to Mikey, saying "Let's get one thing straight. You work for me."
Thoughts:
When I got started with programming there really was a divide between grownups who had to learn about computers at an adult age and us kids who thought programming was kind of natural. I remember getting thrown out of the local electronics store because having a ten-year-old write BASIC programs in there was bad for sales. The customers who could actually afford the computers were put off by a kid like me knowing how to operate them.
Showdown with Mikey's Dad
Georgie's dad who had tried to hack them is still snooping around and calls Mikey's dad. He has detected Mikey's hack against banks. His mom can't believe it.
The family gets into a heated argument which ends with Mikey's dad taking his terminal.
What the parents don't know about is the brand new Zeilemann Starfire 600 laying in Mikey's closet. He gets it out and starts hacking into his dad's accounts using access codes he's been able to shoulder surf his way to. He suspends his father's checking account, savings account, and mortgage account. He continues to kick dad out of his job, zeroes his pension, and cancels his credit card.
Mikey keeps backups so that he's able to restore his father's digital life. But only on his terms which come down to leaving him alone.
He gets his way and everything seems to be back in order.
A while later, his dad removes the hinges to his room to get in and when Mikey tries to get online to again take down his dad's accounts, he has no connection. "I cut your cable down in the basement," his father says.
They send Mikey to a military academy where he is not allowed to access computer networks. He pulls out his Starfire at night and touches the keys, reminiscing the good ol' days with Lisa, Georgie, and Rayno.
Thoughts:
The network being wired is key to the plot here and it's interesting how William Gibson talked about missing the wireless revolution too in his early works. Here's from a 2011 interview with Gibson:
One of the funniest things about Neuromancer, which I wrote in 1984, is that there are no cell phones. If I were a 14-year-old reading it today, I’d be about two chapters in and think, “What happened to all the cell phones?” Becoming quaint so quickly in science fiction is unavoidable. Either we won’t see the technologies that are emerging ahead of us, or we won’t be able to see the uses that people will put them to, which are almost never what they were intended for.
Today, it's much harder for a parent to insta-shut off network access if the kid has a cellular connection. Eventually it comes down to money, since few kids pay for their own cellular plan.
Final Remarks
I'm in awe that Bethke was able to write this in 1980. The banter is great, the use of a network and mobile units is very realistic 44 years later, and the punkness is just enough to make it be underground and feel like cyberpunk.
Modern cybersecurity and hacking is so much more sophisticated than back in the days. The short story's kind of quick access to a plethora of systems and the ability to change almost anything in them feels over the top today. But I have no doubt that it was possible in the eighties.
A rather sad part of Bethke's early work was the contract that he signed for expanding Cyberpunk into a full novel. The editor eventually demanded that he change the ending in a way he couldn't accept and the novel was never traditionally published. Bethke later released his 223-page version as shareware and was kind enough to send me a copy. I'm hoping to get his permission to get it to you in some form so we can all read it.
But Bethke did eventually reach the fame and publication he deserved with his novel Headcrash from 1995. It won the Philip K. Dick Award that year. I'll probably get to it in a future issue of this newsletter.

Currently Reading
I'm still reading White House Warriors:
How the National Security Council Transformed the American Way of War. It's a fascinating story of post WWII US foreign policy and the different personalities of US presidents since 1947.