The Secret History of Hacking, and audio book auditions
Welcome to the February issue of Hacker Chronicles!
I've got lots of things for you this time. An update on the editing of Submerged, a vote on which voice actor should record my novel Identified, a new merchandise store with coffee mugs and t-shirts, and a review of the hacker documentary The Secret History of Hacking.
Enjoy!
/John
Writing Update
I'm almost through editing my sequel Submerged and sending it off to my alpha readers and development editors. I wanted to show you what this looks like so here's one of my four hundred pages with notes:

This is where I am right now, word count-wise:
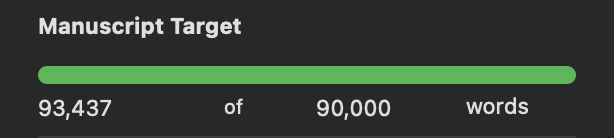 As you can see, my editing has cut more than a thousand words since New Year.
As you can see, my editing has cut more than a thousand words since New Year.
Audio Book Version of Identified
The most frequent request I get is for Identified to be published as an audio book. The other week I was talking to a fellow person in the tech industry and when he learned I'm an author he pulled up Audible to queue up my novel. I had to tell him it's only available as text.
When I got home I told myself that's it — I have to invest in an audio version of the book. The big challenge is how to handle the book's technical content like source code and crypto text. Trust me, it's not fun to listen to a SHA256 hash read out loud (I have, through voice synthesis). But I have some ideas for how to handle it.
Vote on Your Favorite Voice Actor!
I got a project set up and have now listened to over sixty auditions. I'm down to three top contenders and would love to hear who you think I should choose!
You can listen here (spoiler alert for my novel Identified, obviously): Auditions
Then reply to this email and let me know who you liked and why. Thanks!
I'll only leave the audio files up on my server for a week.
New Merchandise Store
San Francisco Writers Conference is coming up in a couple of weeks. I wanted to get the word out about hacker fiction as a genre and created t-shirts to wear at the conference.

In parallel I was getting the audio book project set up and noted the cost of recording Identified. It's freakin' $4,000! That gave me the idea of setting up a merchandise store.
Now you can get t-shirts, stickers, coffee mugs, and even an apron. Each purchase earns me a few bucks towards those four grand for the audio book. But more importantly, you help spread the word about hacker fiction and my writing. I would really appreciate that.
Check out the store here: https://hackerfiction.creator-spring.com
I hope they ship to where y'all live.
February Feature: The Secret History of Hacking
You should watch this 50-minute documentary. It's available on the Internet Archive. The image quality is bad and the audio track gets out of sync a bit, but it's worth it. It's a piece of history with direct references to fictional hacking.
Below is my summary of and thoughts on the documentary.
Counterculture
It has always fascinated me that the hippie movement and Silicon Valley happened in the same place on Earth. Sure, you had hippies in NYC's Greenwich Village but over time the connection to San Francisco grew strongest.
Hippies shocked the establishment and older generations with long hair, smoking weed, a message of love and peace, and protesting against the Vietnam War and the Cold War.

It turns out the counterculture side of hippies played right into the budding hacker culture. First it was about being able to own a computer at all (the rise of personal computers), then the freedom to tinker with them.
Phone Hacking
Up until the breakup of the Bell System, long distance calling in the US was expensive. Young, technically inclined people had a desire to hack the phone system and call for free.
So called phone phreakers figured out that automatic phone call switching used 2600 Hz tone signals to operate. And if you could mimic those signals, you could instruct the phone system to do things for you, such as place a call.
Hilariously, it was discovered that the plastic pipe that came with Captain Crunch cereals could produce that exact 2600 Hz sound and the toy became a phreaker staple.

The most fascinating part of the documentary is that the original phone phreakers where blind, and some of them so skilled that they could manually whistle the tone and pulses needed to manipulate the phone system.
Since phreakers knew what they did was legally questionable, they used handles instead of their names. An early one named John Draper simply took the handle Captain Crunch.
Early Chat Rooms
A cool thing pointed out in the documentary is that phreakers formed the earliest chat rooms. They would set up multi-party phone calls and just chat for free even though it was long distance. This culture later transitioned to things like Internet Relayed Chat, IRC.
Mixing Data and Code
As you might recall from my October 2022 newsletter issue, one of the fundamental things hackers exploit is the mix of data and code in computer memory. Phone switching by tones on the wire is such a vulnerable mix – what should be a pure voice channel was also used for code, i.e. the switching signals.
Computer Hacking
Steve Wozniak who would later found Apple Computer with Steve Jobs was mind-blown by phone phreaking when he read an article in Esquire about Captain Crunch. Since both were in the San Francisco Bay Area, they met up and that's in part how the computer hacking scene and the phone hacking scene got connected. Wozniak started building so called blue boxes used to send tone signals and manipulate the phone system.
Wozniak tells us in the documentary how he was hell-bent on some day owning his own computer, before it was possible. In March 1975, the legendary Homebrew Computer Club was formed. They started their meetings before the first personal computer kit had even shipped, just to discuss what would be possible once they had computers. The club became a hacker haven for enthusiasts who wanted to build, modify, and program computers. It's where he showed off what would eventually become the Apple I computer.
Computers Connecting Over Phone Network
Early networking between computers used the phone network. So it was a natural transition for phreakers to try to hack computers on the other end of the line. This gave rise to what we today call hacking, i.e. breaking into computer systems.
Hacking over phone lines became well-known after the block buster movie WarGames came out in 1983. I've reviewed it here. With that story in the public's mind, it wasn't about pranksters or chat rooms any longer, it was about thermonuclear war.
Hacking Becomes a Criminal Thing
The 1980s is also where the third hacker in the documentary comes in — Kevin Mitnick. He was kind of a loner who gravitated toward solo hobbies. Phone phreaking and computer hacking were great options. He started combining it with pretty intrusive social engineering where he duped company employees to help him get access to system documentation.
Mitnick got convicted for computer break-in in 1988 and served in solitary confinement because the judge was made to believe that Kevin could start World War III if he had mere access to a payphone. A likely result of WarGames.
In the classic hacker movie Hackers from 1995, the protagonist Zero Cool is caught the same year as Mitnick, 1988. He is banned from owning or operating computers and touch-tone telephones until his 18th birthday. And the team of hackers he later joins is big on phreaking and computer break-ins. You can really tell how pop culture and hacking blended back then.
Kevin Mitnick Keeps Hacking
In the documentary, Mitnick tells the story of how he finds his dad's phone tapped once he's out of prison. He starts investigating it hacker-style and gets access to FBI voice mail. They come for him and he goes underground — fake identity and all.
Incredibly, he manages to stay away from the Feds until 1995 when he's arrested. The case against him is so complex that by the time he's sentenced, he has already served four years waiting.
Kevin Mitnick and the US Government's reaction to his deeds formed the view of hackers for two decades, until we got hacker collectives like Anonymous and LulzSec, and then nation state-affiliated ones like Cozy Bear.
After the documentary was shot, Kevin went on to form his own consultancy company and co-wrote four books on computer security between 2002 and 2017. He died of pancreatic cancer just last summer. Throughout his life he remained a controversial figure as well as the face of what I'd call the second hacker generation.
Final Remarks
The documentary is a testament to the origins of hacker culture. Given today's large scale ransomware attacks and cyber warfare, the notion that hacking is about young people pulling pranks feels distant.
Even so, what was once hacking in a legal and curious sense has not died. People do that kind of hacking all the time. The indie developer scene is strong, as is hardware hacking with Arduino, LoRa, and Raspberry Pi.
Currently Reading
I've been reading non-fiction since finishing The Mysterious Affair at Styles by Agatha Christie. Mainly Girig-Sverige: Så blev folkhemmet ett paradis för de superrika by Andreas Cervenka. Freely translated, the title is Greedy Sweden: How a middle class haven became a paradise for the super rich.
It's the tale of how the Swedish tax system was reformed to all but abolish tax on capital gains and properties while keeping taxes on work income among the highest in the world. Sweden now has more than four times as many dollar billionaires per capita as the US. Meanwhile, a tax bracket of 52.6% is reached already at $59k yearly work income.
US law requires me to provide you with a physical address: 6525 Crown Blvd #41471, San Jose, CA 95160