Mr. Robot, Season 1, Episode 1
Welcome to the October issue of Hacker Chronicles!
Fall is here. 🍂 Such a great time of year to read, don't you think?
I got a lot of reactions and thoughts from you on last month's issue about generative AI in writing and the arts. Since then, I've purchased a subscription of ProWritingAid to use its superior grammar checking during my beta read edit of Submerged. I'll report back on how that goes.
I've continued listening to writers and professionals in publishing who are pro AI and the most fascinating glimpse from the last few weeks was the idea of AI voices making it a lot easier to have multi-voice casts for audio books. Imagine a professional narrator telling the story and acting as the protagonist, and then AI voice acting for the other characters. That sounds really appealing to me, especially with the human narrator and the author involved in exactly how those other voices should sound. The same idea will also make it a lot easier for authors themselves to record their audio books since acting different voices is among the hardest parts.
This month's feature is a review of the first episode of the hacker TV series Mr. Robot. It's been on my list to review ever since I started this newsletter more than three years ago. Actually, the first season served as great inspiration for me as I was writing what eventually became Identified. So I'm happy it's finally happening.
Enjoy!
/John
Writing Update
The beta read has wrapped up and I have a spreadsheet full of feedback. I've also gotten quite far in extracting themes from the feedback and planning how to address it.
As was the case with Identified, the beta readers really like the story once they are in it and it's the beginning that's the challenge. How much introduction of characters should there be (vs plunging into action)? How to establish relationship and emotions early on? How much description of scenes do readers want?
I personally like fast pacing and filling in quite a few blanks myself when I read. But when it comes to my own writing, I already have characters, emotions, and scenes crystal clear in my mind, so I can't trust my own judgement on what is enough. Beta reader feedback is great for that.
I will very likely write a third opening chapter and see where that takes me. The original one was cut after the alpha read, not because it was bad but because I got a suggestion for a different starting point.
Where to begin a story is hard. Readers need to get invested enough to continue, the opening needs to pose questions that readers want answered, and readers who've never read this particular author need to get an impression of what kind of book it is.
Quite a few acquaintances have asked me lately when the next book is coming out. I'm still hoping for a January release. The anticipation is growing!
October Feature: Mr. Robot, Season 1, Episode 1
Mr. Robot is one of the most frequent comparisons I get when people speak of my fiction writing. It's a great hacker TV show which aired 2015-2019. It stars, among others, Rami Malek as Elliot Alderson, Carly Chaikin as Elliot's sister Darlene, Portia Doubleday as Elliot's friend Angela Moss, Christian Slater as Mr. Robot, and Martin Wallström as corporate tech lead Tyrell Wellick.
The show was written by Sam Esmail who has a background in tech and venture capital and I've watched interviews with him where he talks about how he wanted to feature realistic hacking.

Reviewing all 45 episodes is too much, so I never figured out how to approach it. Until now, after deciding that I should just pick episodes that I find great to share my thoughts on them.
The first episode is titled eps1.0_hellofriend.mov which is a reference to an Apple QuickTime Movie file.
Spoiler Alert: Yeah, there are spoilers below.
Trailer: YouTube
Hacker Rating
Hacker Realism: ⭐️ ⭐️ ⭐️ ⭐️ ⭐️
Hacker Importance for the Plot: ⭐️ ⭐️ ⭐️ ⭐️ ⭐️
Hacks: ⭐️ ⭐️ ⭐️ ⭐️ ⭐️
Straight A's. What can I say? Let's head in!
Ron's Coffee
Opening scene. The hacker Elliot talks to himself about powerful people in the shadows — the top one percent of the one percent who control the world without us knowing it. He thinks they're following him.
He thinks about how he skipped Angela's birthday party yesterday and instead went to Ron's Coffee Shop.
At the coffee shop, we see Elliot sit and wait for a newly arrived man to find a seat. Elliot sits down on the opposite side of the small table and tells the man that he knows he's Ron, the owner of the coffee shop chain, and that Elliot has hacked him.
Elliot shares how he used to love this particular coffee shop for its immense WiFi speed. Then he got curious as to why such a place had that kind of connection and found that Ron ran a website called "Plato's Boys." It turned out to be an illegal website serving child pornography to thousands of users, hidden on the Tor network. Elliot shows print-outs to prove he has access to the servers.
Ron thinks he's being blackmailed and refuses to pay. Elliot gets up and says he's already sent an anonymous tip to the police. Ron gets desperate and offers money anyway. Elliot heads out and tells Ron he doesn't give a shit about money.
Thoughts
This scene immediately establishes Elliot as a resourceful hacker, a person with his own agenda, a person willing to go outside the law to accomplish his goals, and a vigilante on the side of the people nailing a guy responsible for a hideous crime.
You might recall me writing about the three archetypal hackers in fiction – the vigilante hacker bending society to their will, the professional hacker or mercenary, and the accidental hacker who stumbles upon bad things afoot. Elliot is clearly of the vigilante type.
The Tor network is a way to access resources on the Internet anonymously. To connect to a server over Tor, your traffic jumps through several "nodes" before arriving. The nodes obscure who or what is requesting something from the server and this way of routing internet traffic is called onion routing.
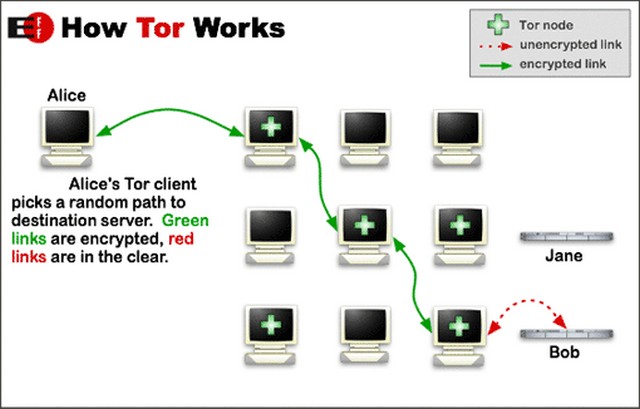
To hide a server like Elliot says that Ron has, you set it up as an onion service. That makes it accessible only on the Tor network.
The RUDY Attack
Elliot comes to work at AllSafe, where he works as a cyber security engineer. His boss tells him their customer E Corp has been hacked again and hands him a stack of paper.
What am I looking at? Is this the log file? This was a RUDY attack. This is awesome.
We see a cut scene with Elliot in psychiatric session, thinking how he's hacked his psychiatrist and knows she's divorced and lonely.
At work, a coworker who is dating his friend Angela comes by his desk and suggests lunch. He's hacked that guy too and knows he's cheating on Angela.
Representatives of E Corp, or how Elliot likes to call them, Evil Corp, have arrived to discuss the latest hack. They are shown around the office space and one of them stops at Elliot's desk. It's Tyrell Wellick, Senior Vice President of Technology. He admires the fact that Elliot is running Linux and mentions that he does too.
Thoughts
RUDY in RUDY attack stands for R U Dead Yet. It's a type of denial of service attack where not too many connections to the target server are opened but those connections are kept open for a long time. The attacker slowly posts data to the server to keep connections alive and consume resources. Slowly as in one character per ten seconds, like this: H (10s) E (10s) L (10s) L (10s) O for a total of 40 seconds to send HELLO. Simplified, that would consume one of a limited number of connections to the server for 40 seconds which is a long time for computers. Expensive for the server, cheap for the attacker.
There's a well-known hacker tool for these kind of "low and slow" attacks called Slowloris.
Evil Corp's logo is a tilted E much like Enron. That can't be an accident.


The name Evil Corp makes me think of Google's former motto Don't be evil. Both Enron and the first days of Google's Don't be evil era are from the beginning of the century. The writer, Esmail, has shared that he wanted to make a film about hacker culture for around fifteen years before Mr. Robot, which came out in 2015. Makes sense. Imagine that lead time!
Being impressed by desktop Linux still rings true. The only ones I know who stick to it are pentesters. They seem very happy with it.
Getting the Psychiatrist's Date's Phone Number
Elliot gets a ping that his psychiatrist just posted a picture on Instagram with her new date. He fears she's being taken advantage of and figures out what restaurant they're at based on the photo. He goes there and waits outside.
The date is over and the man she's dating gets a yellow cab. Elliot calls the cab company and says he's left his keys in the very cab the guy just leaves in. He gets the address the cab is headed to: 306 Hawthorne.
Elliot goes there and finds the guy trying to get his little dog to pee. He asks the man if he can borrow his phone to call his mom since his own is out of battery. Elliot looks young so it works. He goes through the installed apps before calling himself to get the man's phone number.
Elliot deletes his outgoing call from the list before returning the phone.
No answer. Thanks anyway.
Thoughts
Calling yourself with someone's phone is a neat trick. I wonder if people would lend their phone to a stranger. I would offer to make the call and let them speak to their mom in speaker mode, but not give them my phone. That would have still leaked my phone number but not let the person check my installed apps and delete their own phone number from the outgoing list.
Another DoS Attack
Angela calls Elliot 3am. E Corp is being DDoS'ed and she doesn't think their guy on duty can handle it. She needs Elliot's help.
The hack is all over the news:
Massive Corporate Server Hack Worse Than Previously Thought, Sources Say
Unprecedented invasion of secure files shuts down entire system
Hackers responsible for system wide hack unknown, officials say
Elliot gets to the office and checks the status of E Corp's servers. We see this on his screen:
[ping response 1.2s. ; packet loss: 20%]
[firewall: OFF]
[CPU:100%]
status -scanports -s WBUSl12345678WB1 -p[80-7655]
WBUSl12345678WB1 [23.234.45.66]: Unavailable: [80-3456]
WBUSl12345678WB1 [23.234.45.66]: Open: [3457-6555]
WBUSl12345678WB1 [23.234.45.66]: Unavailable: [6556-7987]
status -services -s WBUSl12345678WB1
PID User PR NI VIRT RES SHR S %CPU %MEM TIME+ COMMAND
root 20 0 109m 67m 12m S 1.0 13.5 0:05:21 Xorg
1744 root 20 0 89320 14m 11m S 0.0 3.0 0:00:55 Terminal
1820 root
This is worse than I thought. They're in the network.
Elliot's and Angela's boss says they should restart the services and load balance the traffic.
I don't think this is just a DDoS attack. I think they got a rootkit sitting inside the servers.
Elliot realizes that every time they restart the server, the malware replicates itself during boot up and crashes the host.
By defending ourselves, we ended up spreading the virus everywhere. The only thing we can do is we have to take the whole system offline.
Thoughts
We don't get many details on why servers restarting spreads the malware. Predicting the defensive response and making it work in your favor is a classic hacker move. Perhaps there's some privilege granted to the servers during boot-up that allows the malware to spread.
We see Google+ flicker by on the screens. It's a case of the writer wanting the show to be very accurate but instead becoming prematurely dated. I ended up in a similar trap with how the gas pipeline Nord Stream is featured in Identified. As you probably know, the pipeline got blown up recently.
Elliot's status command seems made up. At least I'm not aware of it. Could be something specific to their server setup.
Flight to Dulles
Elliot and his boss fly to Washington DC where the data center is. All servers have already been taken down and cleaned up. Now they're about to be booted again. Elliot spots something.
Stop. Tell them to stop.
What?
There's an infected server up and running. Don't start the boot sequence. You guys missed one.
Elliot connects a laptop directly to the server.
We need to redirect the traffic. We need to switch DNS.
He configures the bad server to not get the call to reboot. The sequence skips it and the rest of the system can boot up.
I'm going to look at the infected server, OK? Give me a minute.
Elliot thinks the perpetrators must have left a mark. "Every hacker loves attention."
He finds the directory ./root/fsociety/ and under it fsociety00.dat and readme.txt. The readme file contains a message:
---------- readme.txt----------
LEAVE ME HERE
-------------------------------
Elliot's instinct is to delete the file, but he hesitates. Something inside him tells him to leave it there. So he does, and changes the ownership of the file so that only he can reach it from hereon.
Thoughts
Regarding hackers leaving traces, investigators talk about Indicators of Compromise (IOCs). Indicators can be deliberate but an investigator would never rely solely on a hacker claim. They would also look for anomalies such as unusual network traffic, unexplained activity on admin accounts, suspicious files or processes, and the like.
In my view, leaving a deliberate mark is more about threatening or tantalizing the victim.
It's unclear if Elliot is supposed to leave the readme file in place, leave the dat file, or both.
Mr. Robot
Elliot gets on the subway home and a sketchy guy who's been following him shows up. He has a patch on his breast pocket reading Mr. Robot.
The train decelerates. The man who Elliot thinks of as Mr. Robot says:
I'm getting off here. I think you should come with me. But only if you didn't delete it. If you deleted it, we've got nothing to talk about.
Elliot hesitates but gets off as the doors close.
They talk on the platform while waiting for anther train. Mr. Robot is evasive but tells a story of his dad being a small-time thief and proudly telling his son about how it made him free.

A few years after that, they finally caught him. Sent him to jail. Dies five years later. My respect goes with him. I thought he was free doing what he did, but he wasn't. He was in prison. Just like you are now, Elliot. But I'm going to break you out.
Mr. Robot takes Elliot to an amusement park on Coney Island. Their walk from the train station arrives at an abandoned building called "Fun Society." Parts of its sign are gone, leaving only F SOCIETY.

Inside there are arcade games, a bunch of computers, and at least four other people.
A young woman with headphones and heavy eye makeup looks intently at Elliot and shakes her head.
Mr. Robot explains how this place is their whole operation and that all hacking happens there, nowhere else. Confining it to one location means no hacking or communication can be pinned to a team member's location or movement.
Elliot: You said there was a project. What's the project?
Mr. Robot: That'll come later. I just wanted you to see the place.
Thoughts
F Society supposedly stands for "fuck society" which embodies a countercultural or anti-establishment sentiment. I wrote about how the roots of hacking connects to counterculture in the February issue The Secret History of Hacking.
Working from a physical base is cool but risky given that a single team member can be followed there which would take down the whole thing. I assume they use anonymization technologies such as onion routing to at least obscure where their network traffic is coming from.
Framing Colby
Back in his apartment, Elliot searches for Mr. Robot and fsociety online. There are no mentions of either. Fun Society is a defunct arcade since a year and a half, owner shot.
Elliot returns to the arcade and the woman who shook her head at him stands outside, smoking.

Elliot: Where's your boss?
Woman: OK, cut the bullshit. When are you going to give us access to the root directory?
Elliot: What?
Woman: Dude, come on. I wrote that rootkit. I still have to put Colby's IP in the dat file.
Elliot is confused. The woman leaves, calling Elliot a dickhead.
Mr. Robot shows up with twinkies (a snack cake) and mentions that the woman's name is Darlene. They go for a ride in the park's ferris wheel.
Elliot says he's going to turn F Society in but gets cut off. Mr. Robot says Elliot has something else on his mind. Something is wrong in the world and it's about money. Electronic, or virtual, money. Software that processes and handles money.
And, Elliot, we are on the verge of taking down this virtual reality.
Mr. Robot explains that Evil Corp owns an incredible share of the global debt and the plan is to erase all records and cause the world's largest wealth redistribution by effectively canceling all debt.
He adds that Elliot's employer AllSafe will get a visit from FBI and US Cyber Command tomorrow. Elliot needs to put Evil Corp's CEO Terry Colby's IP address 218.108.149.373 in the fsociety00.dat file on the server to stick the attack on him.
The day after, FBI and Cyber Command do show up at AllSafe. Elliot and Angela are called to a meeting about the hack. Elliot is prepared to turn F Society in with the real hacker IP address in the dat file. But during the meeting, Colby is very rude to Angela and requests she is removed as account manager. Elliot changes his mind and pulls out another document, with Colby's IP address implicated. Evil Corp's SVP or Technology, Tyrell Wellick, sees him switch the docs.
Thoughts
218.108.149.373 is not a real IPv4 address since the last segment 373 is larger than 255. Each segment is a byte and a byte can represent 2^8=256 values. The lowest value is 0 and the highest is 255. The reason for using an invalid IP address is probably to not cause trouble for a real IP address out in the world. This TV show has been watched by a lot of hackers after all.
Implicating someone else with their IP address is not strong evidence, or at least should not be treated as strong evidence. Especially if the logs can be manipulated the way Elliot does it. But if there is supporting evidence or there are witnesses, then an IP address could corroborate the implication.
I'm not clear on why Elliot had to leave the dat file in place to be able to plant the IP address evidence. Maybe there's meta data about the file that needs to stay intact, such as creation time stamp? We don't get to see the original content of the dat file. Maybe it contains a lot of consistent data which would impossible for Elliot to recreate so it's better to leave it and just update the IP address in it.
Darlene says she needs access to the dat file. This could be about Elliot's change of ownership of the file which would imply that fsociety still has some level of access to the servers. Or she could mean he should provide her access to the server.
Getting a Dog
Nineteen days pass without any news on Colby or the hack. Elliot decides to pick up the trail of his psychiatrist's date.
He calls the guy named Michael Hansen:
Elliot: Hi, this is Sam from Bank of E security fraud department. Unfortunately, I have to inform you that your account's been compromised.
Michael: What? What happened?
Elliot: First before I can answer any questions, I need to verify some information. Are you still at 306 Hawthorne Avenue?
Michael: Yes. Apartment 2c.
Elliot: Great. And your security question, what's your favorite baseball team?
Michael: Um, Yankees. I don't remember this being a security question.
Elliot: And lastly, your pet's name?
Michael: Um, Flipper.
Elliot hangs up. He will use the details together with a dictionary brute force attack to crack the man's password.

The password attack fails. Elliot realizes that Michael Hansen isn't the man's real name.
He confronts the man outside his apartment building and says he has to break up with Elliot's psychiatrist and tell her the truth, or Elliot will tell his wife all of it, including all the other women and escorts he's been cheating with.
The man accepts. That's when Elliot adds that he also wants the man's dog, Flipper.

Thoughts
Voice Phishing, or Vishing, is a popular attack. Nowadays it's extra scary with AI-cloned voices. I'd say we're already at a place where you cannot trust any voice call, regardless of how much you recognize the voice. Probably not video calls either.
Colby Goes Down
News hits that Terry Colby, CEO of E Corp, has been arrested for aiding or conspiring with hackers to pressure the company during renegotiation of his contract.
Elliot walks the streets of Manhattan, ecstatic. As she raises his arms in triumph, three men in suits forcefully compel him to get into a black SUV. They reach a skyscraper and the men escort Elliot to one of the top floors.
Tyrell Wellick, SVP or Technology at Evil Corp, greets him.
Thoughts
I think we have to assume that other powers are pushing Colby out. A mere IP address would not be enough. And Tyrell Wellick seems kind of satisfied seeing Elliot in that last scene.
Final Remarks
There are some stereotypical things going on here. Elliot is a quirky, lonely, young male dressed in black with a hoodie. That's a hacker trope. Being an undefeatable elite hacker is also a bit tired.
2015 when Mr. Robot came out, several vigilante hacker group activities were fresh in people's minds. There was hacker involvement in Occupy Wall Street, Arab Spring, and Million Mark March. You can definitely feel the origins of F Society in those kind of movements. Nowadays hacker collectives like Anonymous are not as prevalent in the news and we hear much more about nation state hacking.
Elliot's dissociative identity disorder adds depth and plays a large role as the show unfolds. There is some risk of stigma with hackers being introverts and socially awkward but I think it's integrated and given enough space to work. Sam Esmail consulted a psychologist on the portrayal and drew from personal experiences of anxiety and addiction to create Elliot.
I'm looking forward to re-watching subsequent episodes!
Currently Reading
I've started reading Acts of the Apostles by John F. X. Sundman. It's the last of the three novels for which I promised an interview with the author back in the January issue. It's a 1990s edgy hacker story and I'm liking it so far.