The Shell
Welcome to the November and Thanksgiving issue of Hacker Chronicles!
The holiday season is upon us and I’m on the final stretch of NaNoWriMo.
This month’s newsletter feature is The Shell, or command line interfaces and how they show up in hacker fiction. There’s also reason beyond the obvious and that is to set us up for a review of the hacker manga and anime classic Ghost in the Shell in the December issue. Enjoy!
/John
Writing Update
NaNoWriMo has so far resulted in me writing over 17,000 words on my sequel. I’m very happy about that. Here’s a chart of my daily results so far:
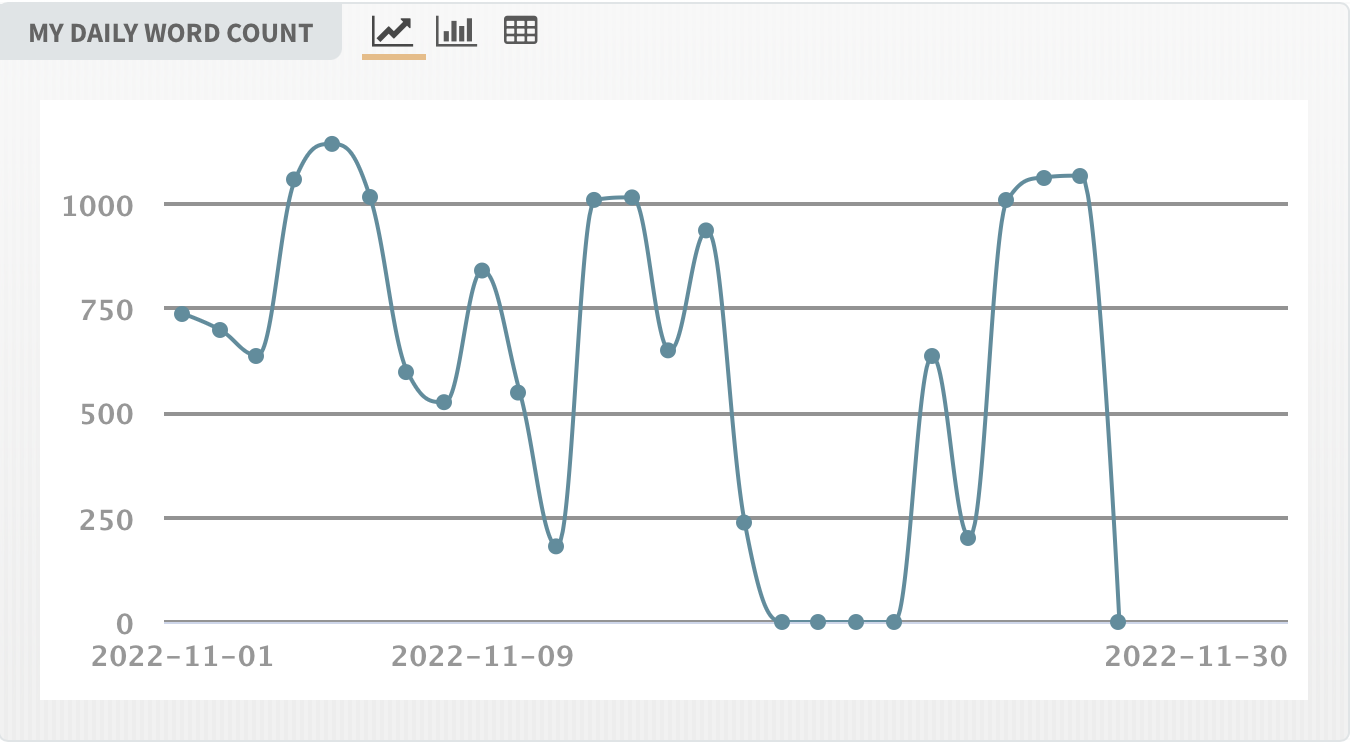
On days off, I’ve tried to write 1,000 words and on workdays 500. The four-day dip in the chart was during a trip to Washington with two friends. We had planned to try local beer breweries up there in 2020 but the pandemic got in our way and only now did we finally get to go.
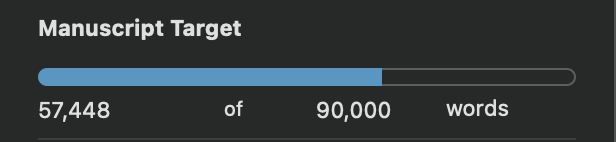
This means I’m now closing in on two thirds written:
November Feature: The Shell
My first computer experience was with a textual interface. I don’t recall if it was a Commodore 64, a VIC-20, or an ABC 80, but they all had it — a blinking caret waiting for me to tell the computer what to do. It was a programming interpreter rather than a shell.
Here’s the BASIC interpreter of the VIC-20:

While not true shells, those interfaces symbolize how interaction with computers worked back in the day, before graphical interfaces became the norm. You would issue commands to the computer in text and get results of feedback in text back.
Real Shells
The Multics operating system was an early version of the Unix operating systems we use today. Its arguably most innovative feature was time-sharing – a way to let multiple programs and users run at once by doing all that they requested in small slices and quick succession. This led us to the term multitasking which has since become something humans talk about in general.
But Multics gave us another seminal thing – the shell. Here’s from Wikipedia:
In 1964, MIT Computation Center staff member Louis Pouzin developed the RUNCOM tool for executing command scripts while allowing argument substitution. Pouzin coined the term “shell” to describe the technique of using commands like a programming language, and wrote a paper about how to implement the idea in the Multics operating system. Pouzin returned to his native France in 1965, and the first Multics shell was developed by Glenda Schroeder.
The original report is available online (pdf), leading with:
SUBJECT: The SHELL: A Global Tool for Calling and
Chaining Procedures in the System
FROM: Louis Pouzin
DATE: April 2, 1965
Shells and Hackers
Shells are very useful for hackers since they provide a low bandwidth interface to a target machine while still granting access to files and powerful tools. The way you demonstrate your ability to hack a system is typically by spawning a root shell or the tongue-in-cheek practice of launching the calculator app as root/admin.
Trinity’s Shell Hack
You may recall from my review of Matrix Reloaded that Morpheus’s team needs to kill power in the Matrix to be able to enter the building where the Architect is. Trinity hacks her way to kill the necessary grid nodes and the hack she performs is actually believable. The global hacker community rejoiced! The Register wrote this back in 2003:
But at exactly the point where audiences would normally be treated to a brightly-colored graphical cartoon of a computer intrusion, a la the 2001 Travolta vehicle Swordfish, or cheer as the protagonist skillfully summons a Web browser and fights valiantly through “404 Errors,” like the malnourished cyberpunk in this year’s “The Core,” something completely different happens: Trinity runs “Nmap.”
Here’s a screenshot of that exact scene:
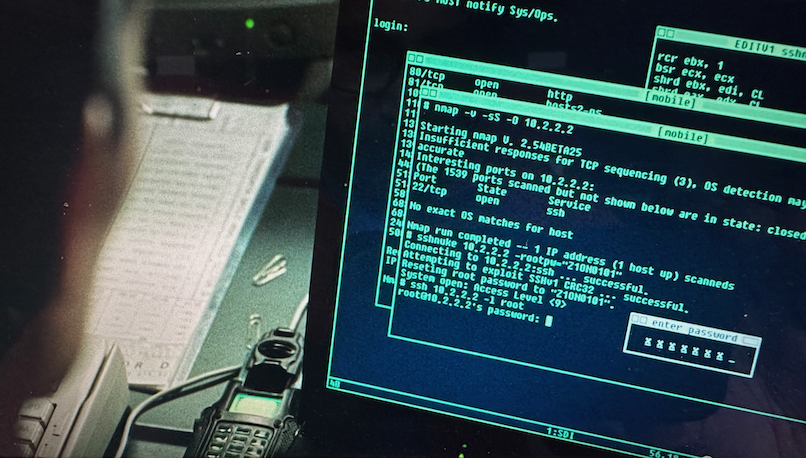
Nmap is a network scanner. It discovers devices and services connected to a network by sending them data packets and analyzing how they respond. Nmap was originally released in 1997 and is still actively developed.
The fact that Trinity uses that tool is pretty darn cool. Here’s my transcript of her shell commands in the movie:
# nmap -v -sS -0 10.2.2.2
Starting nmap V. 2.54BETA25
Insufficient responses for TCP sequencing (3), OS detection may be less
accurate
Interesting ports on 10.2.2.2:
(The 1539 ports scanned but not shown below are in state: closed)
Port State Service
22/tcp open ssh
No exact OS matches for host
Map run completed -- 1 IP address (1 host up) scanneds
# sshnuke 10.2.2.2 -rootpw="Z1ON0101"
Connecting to 10.2.2.2:ssh ... successful.
Attempting to exploit SSHv1 CRC32 ... successful.
Reseting root password to "Z1ON0101".
System open: Access Level <9>
# ssh 10.2.2.2 -l root
root@10.2.2.2's password:
RRF-CONTROL> disable grid nodes 21 - 48
Warning: Disabling nodes 21-48 will disconnect sector 11 (27 nodes)
ARE YOU SURE? (y/n) y
Grid Node 21 offline...
Grid Node 22 offline...
Grid Node 23 offline...
Let’s break the hack down.
The first line is Trinity invoking the Nmap command with four parameters. -v means the tool will output detailed (verbose) information on what it’s doing. -sS tells the tool to run in stealth mode where it slows down and tries to go undetected. -O enables detection of operating system. Finally the IP address of the server she is scanning, supposedly a control server for the power grid in the Matrix.
We do get verbose information, for instance on insufficient responses. Her network scan finds an SSH service open on port 22. SSH stands for Secure Shell so it’s an interface she can connect her shell to for remote access to whatever computer that is.
Then she runs her own attack program sshnuke for IP address 10.2.2.2. If you look at the screenshot above you see a background window with some of the assembly source code of sshnuke. Sounds like she’s “nuking” an SSH service, right? The attack program tells us that it exploits a security vulnerability in the SSH service at 10.2.2.2.
She gives the sshnuke program one parameter. -rootpw means she’s instructing the program to change the password for the root (or admin) account and she gives it "Z1ON0101" as the new password.
We get some logging from the sshnuke program. It successfully connects to the SSH service and exploits SSHv1 CRC32. This is where she gets to change the password of the SSH service. There’s “Nerdy Deep Dive” below those of you who want the details on the exploit. Finally, the nuke program says it reset the root password to Z1ON0101.
From this point, Trinity can log in as root since she now knows the password. She does so and then tells the control server to disable grid nodes 21 - 48 which is pretty clear in its intent. The Matrix’s power grid goes down.
Nerdy Deep Dive (for those who want it)
Let’s explore Trinity’s hack a little deeper.
CRC32 is error detecting code of the flavor cyclic redundancy check.
In 1998, Ariel Futoransky and Emiliano Kargieman discovered a security bug in SSH1’s use of CRC32 that couldn’t be fixed in a backwards compatible way. You can read their original email notification here.
To not create compatibility issues, the SSH1 software was changed so that it would detect attempts to exploit the bug. That detection code in turn introduced another remotely exploitable security bug. This is how that bug was described:
The attack detection function (detect_attack, located in deattack.c) makes use of a dynamically allocated hash table to store connection information that is then examined to detect and respond to CRC32 attacks. By sending a crafted SSH1 packet to an affected host, an attacker can cause the SSH daemon to create a hash table with a size of zero. When the detection function then attempts to hash values into the null-sized hash table, these values can be used to modify the return address of the function call, thus causing the program to execute arbitrary code with the privileges of the SSH daemon, typically root.
Mr. Robot’s Shell Hacks
The Mr. Robot TV series has so many hacks in it that it deserves many mentions in this newsletter. Honestly, I haven’t decided to tackle that series since the early episodes are jam-packed with hacker fiction. My current vague plan is to review the first season episode by episode.
Suffice to say that the main character in Mr. Robot, Elliot, uses a plethora of shell tools for his hacking. His operating system of choice is Kali Linux which is focused on digital forensics and penetration testing. On Kali, Elliot for instance uses the tool spooftoophwhich is designed to spoof Bluetooth devices. With that tool he clones a police car’s Bluetooth keyboard.
There are some excellent reviews of Mr. Robot‘s hacks here.
Shell Hacks in Identified
My novel Identified has several examples of shell hacks. In the chapter “The Privileged Mr. Singh” you’ll read this:
station442$ scp mr_singh@g20s.bc.ca:privEscalate.c .
station442$ clang -o privEsc privEscalate.c
He first copies a source code file called privEscalate.c from the server g20s.bc.ca and then compiles it to run on the border station out in the wilderness between Canada and USA. The joke in the chapter title is of course that Mr. Singh performs a so called privilege escalation attack.
Shell commands lend themselves well to written fiction which I really like. You can convey the details to the reader while staying true to hacking.
The Cyborg Shell
I promised I would bridge this to the epic manga-turned-anime Ghost in the Shell.
The original anime movie is one of my favorites, including its great soundtrack. I’ve had it on my list of reviews ever since I started this newsletter and my intention is to feature it as my holiday special this year, i.e. in the December issue.
So what’s up with the shell in Ghost in the Shell? Two things.
First, there’s no doubt in my mind that computer geeks simply like the mystique around some ghost-like thing hiding in a computer shell. I’ll readily admit that I originally did not understand the title and thought it was a reference to an actual computer shell. In that regard, it’s a lucky and/or clever title. The original title was not considered flashy enough so they changed it to Shell Squad in editing. But the originator Masamune Shirow liked Ghost in the Shell and made sure it was added back as a subtitle.
Second, the real meaning of shell in the manga is a cyborg shell — a robotic shell around a human mind. That’s also the reason for the ghost. It’s not about a Halloween ghost, but about a human spirit. The ghost in the shell is the human core inside a cyborg. This has a deep connection to computer shells because what you get through any computer interface, graphical or textual, is a surface that hides the true nature of the system underneath. The shell may trick you or deny you access to certain privileged parts, just like a cyborg shell.
In the next issue we’ll review Ghost in the Shell for real. I haven’t made up my mind on the split between the manga, the original anime, and the subsequent non-animated movie with Scarlett Johansson. It’s all great hacker fiction!
Currently Reading
I’m still reading Kolymsky Heights by Lionel Davidson. The intense NaNoWriMo has not given me much reading time.