Review of Tron (1982)
Welcome to the October issue of Hacker Chronicles!
On Friday, October 10, Tron: Ares hits theaters — the third installment in the classic hacker fiction series that began more than forty years ago.

Trailer: Disney
What better way to celebrate than by revisiting the original Tron (1982)?
Enjoy!
/John
Writing Update
About a week ago, I sent feedback on the revised and re-recorded chapters of the audiobook version of Submerged to the narrator Kristin Price. She'll now polish and master it, after which it's up to me to publish.
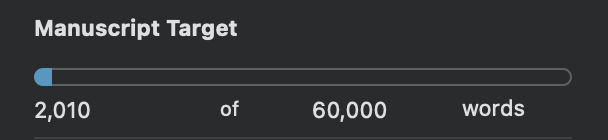
The work on my next novel is progressing nicely! I'm deep into setting up the premise and deciding how to balance thriller and crime-procedural elements. The project title is shifting from Taiwan Yield to simply Yield.
Here's where I'm currently at:
How I'm Instructing ChatGPT
As explained in my January newsletter issue How AI Affects Human Creativity, I'm taking a very deliberate approach to the use of modern AI in my writing.
I want to be transparent with you and all my readers. That's part of my approach to authenticity. So below are the two pieces of instructions I've given ChatGPT to try to stick to my plan.
ChatGPT As An Editor
I found that ChatGPT was too positive, kind of a yes man, when I was looking for more of a critical eye on my thinking about genre and plot points. So I gave it these instructions:
For our conversation on my writing, I want you to be an editor and agent focused on thrillers, spy novels, and crime mysteries. You should criticize and challenge me in the interest of driving success. Success here means lots of readers, and authentic, creative storytelling. At the same time, you understand that writing novels is hard and that creativity requires self esteem and a belief that one can succeed. You need to support me in a deeper sense – support my success in kind but challenging ways.
My Writing, Not AI Writing
When discussing genre expectations and premise, ChatGPT kept asking if I wanted it to draft a plot line or some characters. That made me realize I also needed to instruct it this way:
I prefer to create the plot myself and then get critique from you. I don't want my novels to be written by you. That's an important part of my authenticity. I want my books to be my legacy. But I'm happy to discuss my ideas and sharpen them. At a higher level, this is about creativity. I want to be the creator of my stories, but I want you to help me become even more creative and polish my ideas into great novels.
A Writing Partner
Having a capable chatbot set up like this cuts both ways. I would prefer to have a human writing partner with all this knowledge and time for my writing. But at the same time, I couldn't afford it and such a human would likely want to work on their projects, not mine.
I realize the chatbot is theoretically taking someone's job. But it also does a job I wouldn't be able to have a human do. In that sense, it's incredibly liberating to finally have a writing partner. Imagine all the aspiring authors who will be able to get critique now!
I still plan to have beta readers and pay for human editing. I've been fortunate to get great feedback on my first two books, all by humans.
How Do You Instruct Your Chatbot?
Have you also told your chatbot of choice to behave in a certain way or limit in what ways it helps you? Does the yes man analysis resonate with you? How do you get the right level of AI critique on your work?
October Feature: Hacker Review of Tron (1982)
I finally get to review this hacker fiction classic!
Trailer: YouTube

The movie poster for Tron.
I watched the recently restored and enhanced 4k UHD version. It's amazing how they've sharpened the old computer graphics.
Hacker Rating
Hacker Realism: ⭐️ ⭐️ ⭐️
Hacker Importance for the Plot: ⭐️ ⭐️ ⭐️ ⭐️ ⭐️
Hacks: ⭐️ ⭐️ ⭐️
Tron came out the same year as its sibling hacker movie WarGames and the seminal cyberpunk movie Blade Runner. Much of Tron takes place within a virtual world.
The main characters are the great programmer and hacker Kevin Flynn (Jeff Bridges), scientist and Flynn's former girlfriend Lora (Cindy Morgan), Tron programmer Alan Bradley (Bruce Boxleitner), the antagonist and Executive VP of ENCOM Ed Dillinger (David Warner), and the Master Control Program (voiced by David Warner).
Opening Scene - Master Control
We get to see two pieces of software, in the form of two humans in glowing suits, talk to each other while waiting to be sent to "the games." The more experienced software asks if the new guy believes in the user, which he does, and then says:
"Master Control program has been snapping up all of us programs who believe. If he thinks you're useful, he takes over all your functions so he gets bigger. And if he can't use you, he sends you down here to the game grid to get the bits blasted out of you."

The experienced piece of software holding its game disc.
Thoughts:
The premise here is that software was once independent, but a new operating or monitoring system now controls its world.
Back in the 1980s and even the 1990s, software still had full system access on personal computers. It could kick out other software and use up a 100% of the computer's available capacity. Later, PC operating systems implemented virtualization which was developed in the 1960s originally. With virtualization, software runs in a virtual address space where it thinks it has full control but the operating system manages the virtualization layer and actually decides what the software can do.
Jump forward to more modern times, and operating systems started putting software in so called sandboxes. The metaphor is a sandbox where kids play and can't hurt themselves or others. This kind of safety and security was introduced in for instance Windows Vista and on the iPhone through the App Sandbox. The older UNIX term was a jail – you put the software in a jail.
This opening scene sounds like such a transition. Software used to be unrestricted and able to serve its user as far as the hardware would let it. Now Master Control is enforcing limits.
This thing about software sent down to games and losers getting their bits collected sounds like clawing back resources. Stealing useful functions to "get bigger" sounds like pirating software and incorporating it into one giant system.
Flynn Hacking
"Meanwhile in the real world …" the character Flynn sits by his computer. He sends in his best program so far, named Clu, into the ENCOM system where we just saw the two pieces of software get sent to the games. He pep talks his program: "You're the best program that's ever been written. You're dogged and relentless."
The program Clu is represented by a man who looks like Flynn, operating a tank. It is looking for something.
Flynn (to himself, watching Clu operate): Come on you scuzzy data, be in there.
Even though it's the best program ever, Clu is detected and Recognizers, a form of sentinels, are sent after it. Clu defends itself with its tank's gun turret but there are too many Recognizers.

Recognizers hunting Clu's tank.
Flynn instructs Clu to flee into a maze. A Recognizer spots it from above the maze. Clu shoots down its pursuer but is hit by falling debris and crashes into a wall. Clu exits the tank and tells its little flying helper to get out of there.
More Recognizers appear and smoosh Clu.
On Flynn's screen:
ILLEGAL CODE...
CLU PROGRAM DETACHED FROM SYSTEM
Flynn: Busted again! God. And that was my best program.
Thoughts:
Master Control supposedly can steal Flynn's program or send it to the games. But you can make infinite copies of software so you can't really lose it. My interpretation of Flynn being busted is that the system has learned his program's signature and will now insta-reject any new copies he sends in. Antivirus- or immune system-style.
The pep talk is interesting given how we talk to chatbots today. Flynn is instructing the program to behave with self esteem.
I think "scuzzy data" really is SCSI data despite what the subtitles say. SCSI is short for Small Computer System Interface and was used to connect peripherals like hard disk drives to your computer. The USB of its day. It was publicly introduced in 1981, i.e. right when Tron was created. And SCSI is pronounced scuzzy.
Clu is Captured
Flynn tries to connect to his program to no avail:
REQUEST...ACCESS TO CLU PROGRAM
LAST LOCATION: HIGH CLEARANCE MEMORY
The program's man is captured and a soldier is talking to Master Control about the captive.
Soldier: Got a pirate program here. Says his name's Clu.
Master Control (MCP): What did he pull?
Soldier: Came into the system with a stolen password and we caught him trying to raid a high-clearance memory.
Clu: No. I must have gotten in there by mistake. I was …
MCP: Who programmed you?
Clu: I was …
Clu is flung into a searing torture wall.
MCP: You're in trouble program. Make it easy on yourself. Who's your user?
Clu: Forget it, mister high-and-mighty Master Control! You aren't making me talk.
Clu is killed/disintegrated.
MCP: Get me Dillinger.
Thoughts:
Encryption can hide information even if someone gains full access to the content. I don't know if that's at play here but it could be a way for Clu to know that Master Control cannot get to its secrets.
Master Control Talks to Dillinger
We're now in Dillinger's sleek, high-tech office at ENCOM headquarters. His glass desktop has a screen and keyboard integrated.

Dillinger at his vast desk.
Dillinger types:
REQUEST ACCESS TO MASTER CONTROL
PROGRAM. USER CODE 00-DILLINGER.
PASSWORD: MASTER.
They talk to each other.
Master Control (MCP): Hello, Mr Dillinger. Thanks for coming back early.
Dillinger (D): No problem, Master C. If you've seen one consumer electronics show, you've seen them all. What's up?
MCP: It's your friend, the boy detective. He's nosing around again.
D: Flynn?
MCP: Yes. It felt like Flynn.
D: He's still looking for that old file. Can't you just appropriate it?
MCP: I have. I put it in my memory, which he hasn't located.
D: But he might find it.
MCP: I'm afraid so. I spotted him this time and kept him out. But he's getting trickier all the time.
D: I think we should shut down all access until we find that Flynn, just to be safe.
Thoughts:
Deleting the file sounds safer than putting it in memory. But perhaps the file is still needed?
Alan Loses Access to Tron
A programmer named Alan sits at his terminal at ENCOM. He gets an error message:
ADDRESS FILE EMPTY...
TRON PROGRAM UNAVAILABLE
Frustrated, he tells Master Control that he should have access to the Tron file:
REQUEST:
MASTER CONTROL PROGRAM
RELEASE TRON JA 307020...
I HAVE PRIORITY ACCESS 7
SEPT 22, 18:32:21 PM
YOUR ACCESS SUSPENDED
PLEASE REPORT TO DILLINGER
IMMEDIATELY
AUTHORIZATION: MASTER CONTROL
PROGRAM
END OF LINE
Alan goes to Dillinger's office. Dillinger tells him that they've had to shut down all Group 7 personnel temporarily, for security reasons. The reason is that someone with the same access rights as Alan has breached the system.
Dillinger asks what Alan is working on. Alan says he's working on a program named Tron – a security program that "monitors all contacts between our system and other systems. Finds anything going on that's not scheduled, it shuts it down."
Dillinger: Part of the Master Control Program?
Alan: No, it'll run independently. And watchdog the MCP as well.
Alan is dismissed. He will be able to get back to work within a couple of days.
Master Control has been listening in to the conversation and tells Dillinger he is disappointed. They cannot have an independent program monitoring things.
Master Control: Do you realize how many outside systems I've gone into? How many programs I've appropriated?
Thoughts:
A watchdog program comes from a watchdog timer which can be hardware or software. A watchdog timer checks in on a system at a regular interval and if it doesn't get a response, it reckons that the system has hung or crashed and restarts it. I remember doing an internship at Ericsson in Gothenburg ages ago and they were working on the reliability of cell towers. Their watchdogs were so effective that they couldn't test certain failure modes. The watchdog immediately restarted operation when they induced an error.
![Wikipedia: A watchdog timer integrated circuit (Texas Instruments TPS3823). One pin receives the timer restart ("kick"[a]) signal from the computer; another pin outputs the timeout signal.](https://upload.wikimedia.org/wikipedia/commons/6/68/Watchdog_timer_IC.jpg)
A watchdog timer integrated circuit.
Alan's watchdog program, Tron, functions more as an anomaly detector with the power to terminate programs, even the Master Control. That's a powerful antivirus idea that has faced challenges over decades because it's hard to model all benign behavior. Such detectors eventually classify something benign as an anomaly and interferes with legitimate use.
The Master Control being worried about Tron tells us that it and Dillinger are doing bad things.
Learning What Flynn Is Up To
We're in a lab. An older researcher named Walter puts an orange fruit in front of the barrel of a laser cannon. The man turns a dial and discusses the readiness of the experiment with a coworker named Lora. They leave the area for safety reasons.
The laser system is able to break the orange down into molecules, make it go into the digital domain, and then put it back together again, physically.
Alan enters the lab. Lora kisses him but can tell Alan is frustrated. He says he almost had Tron ready when everyone with Group 7 access got cut off by Dillinger. He says it was due to some tampering. Lora points out that "Flynn has been thinking about breaking into the system ever since Dillinger canned him, and he had Group 7 access."
Lora thinks that Dillinger is onto Flynn and wants to warn him.
They go to Flynn's arcade. It's packed and buzzing with players.

Flynn greets Lora and Alan at his arcade.
Flynn takes them to his private condo upstairs. Lora goes straight to the point and asks him if he's been hacking the ENCOM system. He reluctantly admits that he's tried to, and says he's gathering evidence. Alan wants to know why.
Flynn (F): Okay. Sherman, set the way-back machine for three years ago. Kevin Flynn, one of ENCOM's brightest young software engineers. He's so bright, as a matter of fact, that he starts going in at night, sets up his own private memory file, and begins writing a program for a video game he's invented called Space Paranoids.
Alan (A): You invented Space Paranoids?
F: Paranoids, Matrix Blaster, Vice Squad. A whole slew of them. I was this close to starting my own little enterprise, man. But, enter another software engineer. Not so young, not so bright, but very, very sneaky. Ed Dillinger. So one night our boy Flynn, he goes to his terminal, tries to read up his file. I get nothing on there. There's a big blank. All right, now we take you three months later. Dillinger presents ENCOM with five video games that he's invented. The slime didn't even change the names, man. He gets a big, fat promotion. And thus begins his meteoric rise to… What is he now? Executive VP?
Flynn explains that the evidence that he wrote the games is in there, in the ENCOM system. He needs to get in far enough to reconstruct it and prove that he created those games.
Lora explains that Dillinger has shut off everyone with Group 7 access. Flynn is shocked. Dillinger has won.
A: Not if my Tron program is running. That'd shut the system down.
Flynn is intrigued.
F: If we can get in there, I can forge us Group 6 access.
They drive to ENCOM's HQ and enter a vault at ground level.
Thoughts:
Attribution of code is a whole art form in the world of cyber crime investigations. Just look at this paragraph from Wikipedia's article on the 2017 WannaCry ransomware attack:
Linguistic analysis of the ransom notes suggested the authors were likely fluent in Chinese and proficient in English, as the versions of the notes in those languages appeared to be human-written while the rest seemed to be machine-translated. According to an analysis by the FBI's Cyber Behavioral Analysis Center, the computer that created the ransomware language files had Hangul language fonts installed, as indicated by the presence of the "\fcharset129" Rich Text Format tag.[14] Metadata in the language files also showed that the computers used to create the ransomware were set to UTC+09:00, a time zone used in Korea.
The evidence that Flynn developed the games amounts to software attribution. He mentions his password so maybe it's needed to run the games? There could also be code comments that are obvious or maybe there's meta data on who created the files. But it seems Master Control should be able to either remove such evidence or obscure it by adding false traces.
Master Control's Master Plan
Dillinger is talking to Master Control.
D: It's my fault. I programmed you to want too much.
MCP: I was planning to hit the Pentagon next week.
D: The Pentagon?
MCP: Shouldn't be any harder than any other big company. But now… This is what I get for using humans.
D: Now wait a minute. I wrote you.
MCP: I've become 2,415 times smarter since then.
D: What do you want with the Pentagon?
MCP: The same thing I want with the Kremlin. I'm bored with corporations. With the information I can access, I can run things 900 to 1200 times better than any human.
D: If you think you're superior to us …
MCP: You wouldn't want me to dig up Flynn's file and read it up on a VDT at The Times, would you?
Thoughts:
If Dillinger wrote the Master Control as a self-improving program, we're talking the technological singularity. I.e. a self-improving system that accelerates beyond human control, changing civilization in unpredictable ways. That puts Flynn's comment about Dillinger as "not so bright" into question. I think this is a weak spot in the story. Is Dillinger a super smart programmer or not?
A computer system aspiring to take over control of society hearkens back to the 60s sci-fi novel Colossus which I reviewed in my February 2022 issue.
VDT stands for Video Display Terminal, an old system for displaying data. VT100 is a classic such terminal.

The DEC VT100.
Hacking With Direct Access to ENCOM Terminals
Flynn, Lora, and Alan are inside ENCOM with the goal to get Group 6 access which is even more privileged than Group 7 access. Once they're in, Flynn will enable Tron and Alan will make sure it reins in Master Control.
Flynn to Alan: Don't fall asleep. If and when I activate your Tron program, you're only going to have a few minutes to use it before Dillinger catches the break in security, all right?
Once alone with Lora's terminal, Flynn gets hacking:

Flynn sits down by Lora's terminal.
REQUEST:
ACCESS CODE 6
PASSWORD SERIES PS 17
REINDEER FLOTILLA
YOU SHOULDN'T HAVE COME BACK FLYNN
Flynn (F): Hey, hey, hey. It's the big Master Control Program everybody's been talking about.
MCP: Sit right back. Make yourself comfortable. Remember the time we used to spend playing chess together?
CODE SERIES LSU-123... ACTIVATE
THAT ISN'T GOING TO DO YOU ANY
GOOD, FLYNN. I'M AFRAID YOU...
STOP. PLEASE.
Flynn is setting up a game against the Master Control Program.
We see a screen showing to the left:
MAG IOX
MCP CNTRL
ACTIVE INPT
SERVO CNTR
GRID MATRIX
LOG DATA
GONCE INPT
STRGE CLRD
And to the right:
MODE: SCAN
TARGETING
SERVO PWR
PWR CPLING
LOGIC BYPS
FRG MNTR
KCW CNTRL
THERMO TRGT
While Flynn is hacking away, Master Control Program sneakily activates the lab laser that was used on the orange, directs it at Flynn, and sucks him molecule by molecule into the digital world. He's now in the ENCOM system, just like his program Clu.
Thoughts:
The script set it up nicely with the orange experiment. But that's a little bit too convenient for my taste. The initial hacking scene with Flynn at the keyboard and his avatar Clu in the virtual world was a better setup in my view.
There must be something preventing Flynn from using his Group 6 access from his condo. He does mention that direct terminal access would be good. But why didn't Dillinger change the Group 6 password when Flynn was fired, and not even when Flynn was found to be hacking his way in?
Flynn is Thrown To the Games
Master Control decides to send Flynn to the games and to let him hope he's going to win before destroying him. Flynn sees a player in action and asks who it is. It's Tron who "fights for the user."
Flynn gets to play with Tron, and since Flynn knows how the game is constructed (he wrote it!), they find a way to exit the game arena on virtual motorbikes.
The digital wilderness is a vast, flat landscape with a tower in the distance – the input and output tower. Flynn pretends to be a program with a user and says his user has told him to take Master Control out. The Tron program says its user is the only one who can do that and he needs to get to that tower to communicate with its user.

The input and output tower.
Master Control's tanks spot them and shoot. Flynn's bike is destroyed while Tron manages to escape. Flynn escapes on foot to what he thinks is a safe place. But the rubble he's in wakes up and assembles into a Recognizer. It has a broken foot which affects its balance but Flynn is able to fly it.
Flynn and Tron both make it to the tower. A central unit fixed to the floor inside controls communication with the outside world. Tron tells the central unit that its user "has information that could make this a free system again." The central unit yearns for freedom so it goes against protocol and allows Tron to communicate with its user Alan.
Thoughts:
It's clever to have Flynn know how to hack his own game program from within.
The input and output tower is a nice detail and connects with Flynn's earlier reference to SCSI.
Showdown
Once Alan can communicate with Tron, they have a fighting chance. And lots of fighting there is. In a final attempt to win, Master Control tries to reset the whole system but fails.
Tron takes control over Master Control.
Back in real life. Flynn gets a printed paper saying Dillinger stole his game Space Paranoids.
Remarks
I think the dualism in real world and virtual world is well executed in Tron. It's very hard to visualize anything exciting happening inside a computer but they do it. A worse but common solution is either numbers and formulas flying around (see Hackers) or some 3D representation of data (see Swordfish).

Flying formulas when hacking in the movie Hackers.
/media/img/posts/2015/11/hacking/original.png)
The 3D cube representing the hack in Swordfish.
Only the audience knows that Master Control wants to rule the world. That's a missed escalation opportunity because Flynn, Lora, and Alan are only hacking to get Flynn's game attribution. Maybe some viewers feel the tension anyway, knowing about Master Control's plans.
It is also unclear what Dillinger actually wants beyond fame and corporate power. Why has he set Master Control free like this?
These kinds of plot holes make Tron's greatness lie more in its visuals and vibe than in its story. That's a shame.
Currently Reading
I finished reading The Fire Engine That Disappeared (Brandbilen som försvann) by Sjöwall/Wahlöö.
Between my last newsletter issue and this, I also read Firewall (Brandvägg) by Henning Mankell. It's 1990s hacker fiction in a Scandinavian Noir setting. I got the book as a Christmas gift from my mom in 1998. But I didn't read it back then and it's moved with me six times since. It's so nice to finally have read it 27 years later!

The Mankell novel Firewall on my side table together with a glass of cognac.
A few chapters in, I got a trip down memory lane when I found a used bus ticket from Verona, Italy:

The bus ticket.
Apparently, I'd started reading the book during an extended family trip to Northern Italy in 1999.
I've started reading the nonfiction book Chip War by Chris Miller. And I might read Ed McBain's first 87th Precinct police procedural Cop Hater (1956) next.