Randomness, and a new cover for Identified
Welcome to the August issue of Hacker Chronicles!
The backside blurb of The Hacker's Dictionary from 1983 says that the book is "a Berlitz to the underground world of the hacker culture, behavior, eating habits, moods, and assorted computer-jock values." It spends a whole page on the words random and randomness. If you've read Identified or are versed in cryptography, you know that randomness and pseudo randomness are pillars of cybersecurity. That's why this month's feature topic is randomness.
But first I'm delighted to show you what will soon become the new cover of my novel.
Enjoy! /John
Writing Update
I got such great feedback on the cover of the Binary Release of Identified that I've been wanting a new one for the general release by the same designer, Peter Karlsson. Now that has come to fruition. Check it out – it's gorgeous!

I've also continued writing the sequel to Identified including a key plot point and an intense scene in a corridor. I'm a third of the way to my first draft! Here's where I am:
August Feature: Randomness
Nerdy topic, I know. But I think you'll like it.
Think of a sequence of ten random numbers between 1 and 9.
You know I'm going to tell you that the sequence you chose was not so random, don't you? We'll get to that. But first, why is randomness so important for cybersecurity?
The Importance of Randomness in Cybersecurity
Modern computers can perform mathematical operations at an incredible speed. For years now, we've measured top speeds in petaFLOPS, or quadrillion operations per second. That's thousands of trillions.
Such power can be used to encrypt and decrypt data fast enough for humans to not even notice. But that computing power is available to both defenders and attackers.
The way a defender wins the game of computer power is to base cryptographic protections on large random numbers and forcing the attacker to test every possible number to be guaranteed to find the right one. Searching through all possibilities is called a brute-force attack and West and Jitterbug attempt one in my novel.
The defender's large random number is used to form a cryptographic key. Here is for instance Microsoft Security Response Center's public key:
-----BEGIN PGP PUBLIC KEY BLOCK-----
Comment: User-ID: MSRC (Microsoft Security Response Center) <secure@microsoft.com>
Comment: Created: 10/28/2021 3:37 PM
Comment: Expires: 10/28/2023 12:00 PM
Comment: Type: 4,096-bit RSA (secret key available)
Comment: Usage: Signing, Encryption, Certifying User-IDs
Comment: Fingerprint: CB2C563AE4D614152198E11195ED49E4FB340B9D
mQINBGF7Jh4BEACpHPtDpZ2yPbpvwxCZqpxHUIKMETlzqYH8FA/Pl3gfv2yjV4No
ib4MZqvQtMpwTtXemLKqEENKLCo8Xu+NOWhU33fm4h13PrwZFNEOY6SIUkoYR3AP
aK3MEYsm2rJMN4FFSJr/+LeegfPfupPtFVQdCO1YTd9Kik4MGHs6DtkdP7ZIGyNX
6kTEQtDAEZUVvurrg7dPD+BBKZ1xxqB/fOJp++5B9VJIPsp4OW4zmdPrUp52Jm5D
Gg6k3gReXXvLNegw9DrnuqZekxLg1GCQF69sFyP69xWNV2BVTQYKtn5ctzt4b92N
tUDvoXFc3GKM6iWNhoxgTMhcy84QtrJIwpkG7xDC4zKBiRHtADp6uivZF7wxEyUg
+xn3KhTy62YAAZCgzvsbdz5VCthEIXiy0RnAnvR1zE10Gm9y+m3Be54K4WekJTkD
m5U34bstwR8uFTotpcatDZ4APmgweykrafgYjcZHwzjBYpfaxO3oJ/+mRJ+Wt5Y6
pLu9ldKXUheK+GM91tLTp8VFlzX0wzwfiUFya3Bd7FmMLVBabGrkeuA6WaVGFP62
nEZOqY0X6pqOZ6TimfIVLeTFN7a2N7GDsVqH0CezUHftSO/9T+xT8h2/1QVu62Kw
Cj086p+NNK/41P0MzsfvJokOWzrATSCI0iiz4IpVB1EitWyBfOjBJpcv2QARAQAB
tEBNU1JDIChNaWNyb3NvZnQgU2VjdXJpdHkgUmVzcG9uc2UgQ2VudGVyKSA8c2Vj
dXJlQG1pY3Jvc29mdC5jb20+iQJUBBMBCAA+FiEEyyxWOuTWFBUhmOERle1J5Ps0
C50FAmF7Jh4CGwMFCQPCNBIFCwkIBwIGFQoJCAsCBBYCAwECHgECF4AACgkQle1J
5Ps0C50WzA/7BXo8m0F254H9ysyS/ROwcwCg0CaU2JRAhdmd53qzjPo4L5+8h0Vm
1FzdMH1qyimBLDojc/V8anJuLwghdJqidr6mUvj55bLnLOkoUQjFzx3V8eoeI2DY
AyH8UCJCLQAKxmbDssVETWNt8rkSz4t8qbFbWZfsmmjYEuU2TosPX/a/c59rI+L/
eiw+cYegwiYHJca6t2/T8aBMKkX9Eqqy7CvRIoBR4tKpcecUCm1z+z8I0T0a4iPG
8RAHDwW1PGcTqKoxm6iPsraOhBGVaX2Y/pW0tk8/gMxC9uJv8XGbrPzcxnO+wRg9
RMq28vpP8LAoQrA9EDmJSOBdpOfMlYcniNCgfD/o+gJirYEcnUJSJm4zO2kM01vA
iIhgs6Ytm0gi2UNurr6VLPuRleYqzIqwxliB6McmSLLF5t6/oVN/kCtVMTWvDNd5
tBuBUUzzAkPQBX3X8P2qfw+faGXrWdnXQuSW09smH+IV7gE0uIEH2V9F/oXmbVF3
/WWNZ/7HYFDffwJ8QkGWdQPc8Q+MwMYBgxyebNGFIR1953BWyriRWRz7e/JQJpAM
Wtozs4CvfFkqkW4I5MFx2AAUEPKVt+9XTWGNTZ0I7x9C+lYgeFmycZ0Av6U4T978
pkKqpZFGpvFUD6SOIsSLtyPkvSbRtYcqNh3ee9bNNAL3ZSxxIxA831a5Ag0EYXsm
HgEQAL2xH/UXYJLOB9/Y9caqHUVwTUnpX7ukNkYZk70aBDKKTdkSkjZQvFCyCpUw
KsQqzcwdFI9vz2q85m2B12Ct/MRlEWYnRhE4MQeVQCN6hvSys7ES99HgpUucc0fh
PxLyqv0J7jjxLN1o4sGkWZ4CqhpEI/ImFobCRFzzOHOOJubkbjw6GbiZ3cQM+cm/
Wc3e78ryZrD1vqCAl8VRj31X4TJJs188dry0ESoGin5vvZtKSWVE5p7GRyhDodSa
Ob0MZwfFge/NnxzN9WsDVBkD2wicwIxAvad1dBiiJ7m/QQfmEZ4bXW5QqvSYXwqx
lyrl9MzPbQbtw27Oy4xFjgBizSSJDg//X5COcCn+aVzFLlAQlxEWAWucs3bJ5kUm
uBNz1pExhGHqjEVJlElqe17v82+2jOkIlUdn3+A4WjVXkbdOA4eza+VlzqgIRG5p
rO5L6ex679OvF9qQJDSLqzbdB89xynfap5kaoXYEz6ZzJM10rjhOa3K+e54kPESo
1sJOUuShyKdkuVJk+hiwRzaanPplMyVoXvY+LU3QlNvILM6hgBwvoGdwRQjKwjNl
rjG8MbC+z5uGnoIPIa16AUuMtq5CDFzV0dHFqvfBoHV3ocw4ac4dHJYKcrTvj11J
MhBQMhMAZQZ0Ddzg+INR0RDGRUgwyi4xtBU1VXaIMkd6w/U5ABEBAAGJAjwEGAEI
ACYWIQTLLFY65NYUFSGY4RGV7Unk+zQLnQUCYXsmHgIbDAUJA8I0EgAKCRCV7Unk
+zQLnQmHD/9tmzW+XWCNk644mskKTZF1xMoVElqzVoKNfEXN56vdZbgVIRQXefDN
eoSkupSKbOtG3bUC2HXZLBi5RvtQf86kDlJzPPsAonpBV/AMFwSI2TbNkDyYU/A4
WQ3aL6bg7p+1FwBqbnKJZES2tw4qLGDLBrGcrt3mqli+PmMIsTqwtkllo+Xx8HNz
sUO1Me0W5DNgt1Y5T7g8FswERrQRlwXvObe1kmUh6bQ4xzFIasxboyJxjt1ZOl+Z
kmZfPkWto/xC0KO2AUK8Zc/TaoIQ/7CSw0y36mcqAU0EyNAHUboDMxAl2WFt35eO
RZoox+8thUEppC7xmQC78/DQVXbF9/fPiZEv8Spt/J2OT6OKilgCB9FO5VtHGr18
9Gmc95PyWoOXkjUZlTMkRcQ0tGBa9FD5bN5v8nK+lqoTzJfMgXTl3m2whfTwsiN6
HOSl14Bpwgz1glEInOqTj+WZX2ngHZVQbS+gSZjGRl2OKuBIj3RKcTojBCvSm7LI
c3X2ZprDq2kB1hwNZrzz3QxXws2pAXI2gtfJ4JxfyS/dLYcTtR10M/00RaHRZqBU
qjdKj5w3fje1JAbfoO8BBOuhxl/t/Cmul61GEnmMjCJH7fPhsTGa+AuZc/Ycbh+1
tj6cbAqflrlpAlifh1E/cSYEZ0oDmpOv4quMkS9hL/gYQqSVT2LEHw==
=+hjx
-----END PGP PUBLIC KEY BLOCK-----
The above gives you an impression of the size of a random key for modern cryptography. A public key is not a secret, so the above is not a leak. However, only Microsoft has the corresponding secret key which absolutely must not leak.
Even at the speed of modern computers, it will take years and years to find the secret key if the computer can't do any better than guessing. That challenge for the attacker is foundational for cybersecurity.
Is it Really Random, Though?
Let me pose a philosophical question: Can a logic machine like a computer pick a number at random?
Computers are strictly logic. If you know the current state of a computer and what input it's getting, you can predict what it will do next. So how can that ever be random, or produce something random?
That that is a challenge for cybersecurity and my novel has a fictional rework of a real world attack against poor computer randomness.
A Random Seed
To get real randomness, computers need to sample the physical world around them. They do that with a randomness extractor to produce a random seed, i.e. a random starting point. From such a seed they can generate a stream of pseudorandom numbers.
A few possible sources of physical randomness to extract:
- Temperature
- Light
- Sound/noise
- Artifacts from imperfect electronic components
- Radioactive decay
- Background noise from space
A cool website is RANDOM.ORG which offers true random numbers to anyone. There you can for instance roll dice based on randomness from atmospheric noise. Look, I got a double four!
Pseudorandomness
OK, let's assume the defender's computer has sampled a real random seed. From that point, it runs an algorithm called a cryptographically secure pseudorandom number generator. It's a computer program that starts with a seed and then does a bunch of shuffling and scrambling to stretch the random seed into a long sequence of pseudorandomness. It's called pseudo because only the seed is really random, the rest is deterministically generated and if an attacker can get the seed, they can generate the same sequence as the defender.
Let me use a very simple example to explain this. Our simplified algorithm to produce the next number will be seed * 218 / 3 - 5. The leftmost digit of the result becomes the seed for the next round and the rightmost digit of the result is the next pseudorandom number in the sequence. Say the true random seed is 4. That would produce this sequence: 6, 0, 8.
4 * 218 / 3 - 5 ≈ 266 (2 is the next seed, 6 is the random sequence number)
2 * 218 / 3 - 5 ≈ 140 (1 is the next seed, 0 is the random sequence number)
1 * 218 / 3 - 5 ≈ 68 (6 is the next seed, 8 is the random sequence number)
6 * 218 / 3 - 5 ≈ …
It's easy to see that if you know that the pseudorandom number generator is seed * 218 / 3 - 5 and you know the seed is 4, you can figure out every subsequent pseudorandom number. Now, seed * 218 / 3 - 5 is of course not a cryptographically secure pseudorandom number generator, but the example helps to understand the logic.
Any pseudorandom number generator eventually creates loops where it starts the whole sequence over again. In our naive example seed * 218 / 3 - 5, that actually happens the next round where 6 * 218 / 3 - 5 = 431 and the seed becomes 4 again. So that algorithm would produce the pseudorandom sequence of 6, 0, 8, 1, 6, 0, 8, 1, 6, 0, 8, 1 …, repeating itself after four digits.
If an attacker can control or steal the seed, they can generate the defender's secret keys. Game over.
Attacking Randomness in Fiction
Let's turn to the fictional world.
As seen above, randomness is a key(!) piece of cybersecurity and true randomness is a challenge for the defender. This opens up for all kinds of cool cyberattacks in fiction.
The attacker can make the defender's machine pick a certain seed. For instance raise or lower the temperature where the machine is, add noise to the environment, or compromise the way background noise is sampled.
Even if the attacker can't control the seed, they may be able to reduce the true randomness in the seed. You saw that in Identified when West and Jitterbug made sure they knew the time the seed was chosen.
An additional idea that I've been toying with for my writing is to have the attacker try to trigger a sequence loop. It'll be hard to explain but it could be an intriguing plot point.
Our Brains' Ability to Generate Randomness
Finally, we get to our human brains' capacity as random number generators. Are we any good? Can we be hacked?
In 2012 German and Swiss researchers published "Analysing Humanly Generated Random Number Sequences: A Pattern-Based Approach" (pdf). Participants were asked to generate a random sequence of 300 digits 1 to 9. The researchers then looked for patterns that were unique to individuals.
Here's an illustration from the paper:
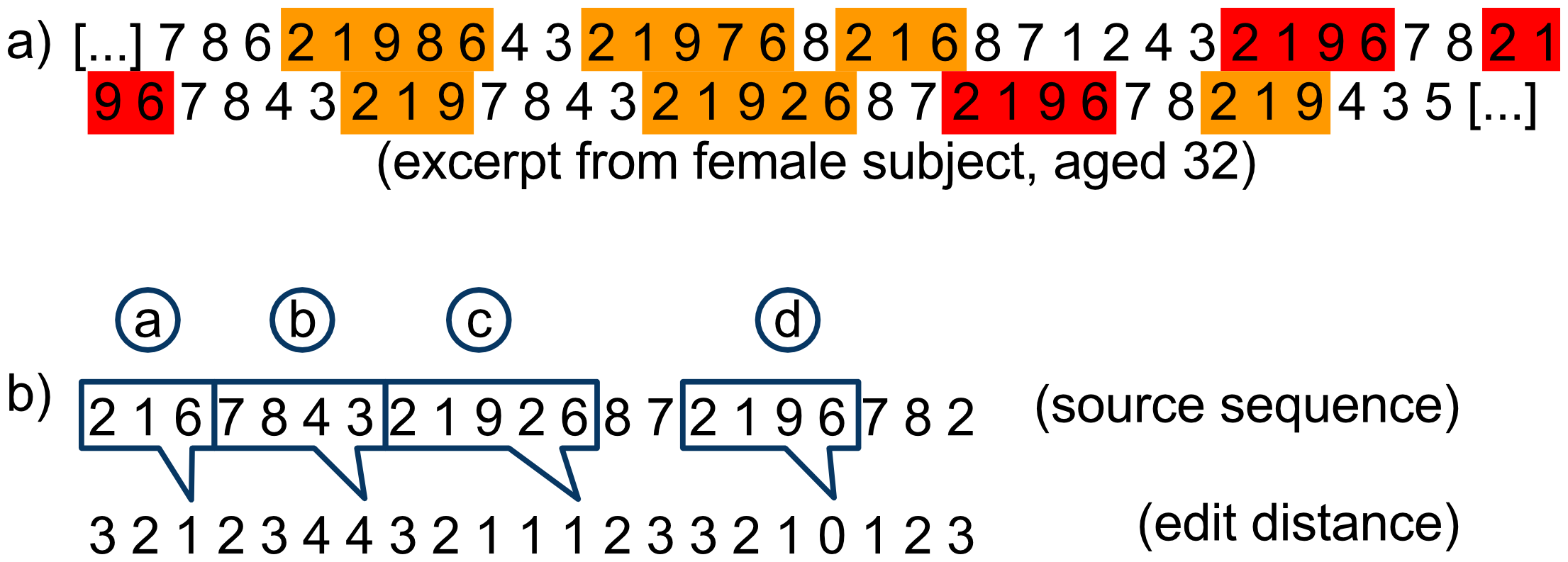
The red highlights show perfect matches for a particular subject's predominant pattern of 2, 1, 9, 6. The yellow highlights show instances where the subject produces patterns that are just one digit "away" from 2, 1, 9, 6.
The subjects varied in their predictability between 14% and 46%. It was also possible to do the reverse – predict who the human was based on their sequence of digits. Now that's something I'd love to weave into a hacker fiction plot!
Currently Reading
I'm still reading George R. R. Martin's A Dance with Dragons. But I've also started reading The Adventures of Tom Sawyer for our oldest daughter.