Pass Thoughts – Authenticating with brain waves
Welcome to the July issue of Hacker Chronicles!
I hope you’re all coping with the heatwave that’s hammering the northern hemisphere. It’s been as hot in Sweden as it is in the San Francisco Bay Area, and Sweden is at the latitude of Alaska.
This month’s feature goes into thoughts and research related to my novel Identified, namely being able to authenticate through brain waves, or pass thoughts. Enjoy!
/John
Writing Update
It was harder than I thought to allocate time for writing during my vacation. This lack of writing made me think of my main piece of advice for those asking me how to write a novel.
It takes enormous amounts of time to write and edit your first novel. Say a thousand hours. Add to that all the time you spend studying the subject of creative writing. You’re learning a new profession. When faced with that time commitment, many decide that they prefer to do other things than write every spare hour they have. 🙂 I think you have to enjoy writing and editing for it to be worth it.
As for me, luckily the jet lag on my return allowed me to start getting up early in the morning. That’s when I’m most productive. So now I’m spending significant time writing again.
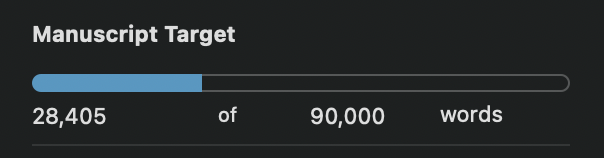
Here’s where I am in writing the sequel to Identified:
July Feature: Pass Thoughts
Time for an installment of research I do for fiction writing. Before we get to pass thoughts, we need to get down to what authentication is and how it relates to identity.
One of John’s Pet Peeves
I’ve been annoyed for over ten years about overuse of the term identify and overuse of actual identification of people in society. When you identify someone, you learn exactly who that person is in physical life. And it turns out that very few things require identification.
Let’s look at an example.
- A police officer stops you in your car and wants to see your driver’s license.
- You produce your license and the officer checks it to see that it’s a valid, real driver’s license and that you match the photo. This is called authentication. Your license is checked for authenticity and validity in the country/state you’re in.
-
The officer checks that the license is for driving a car and not a motorbike. This is called authorization. They have already established that the license is valid and belongs to you. Now they check what the authentic license authorizes the you to do.
Our example should stop here. The police officer is done and you should be on your way. But it doesn’t.
-
The officer now reads your name, birth date, and in some countries your home address, place of birth, or immigration status. This is called identification. But there is no need to identify you to check that you’re allowed to drive. Society keeps mixing up authentication+authorization with identification, and our privacy suffers for it.
Another popular example is when someone needs to check that you’re allowed to buy alcohol. That is a yes/no question. They don’t need to know your precise age, just that you are over a certain age. But again we are often required to identify ourselves to buy wine instead of authenticate+authorize.
This problem is woven into my novel Identified. If we build a society where people are required to identify themselves all the time, the slippery slope of surveillance is there. Those databases should say “Someone over 21 bought wine,” not “John Wilander, age XX, living in San Jose, Swedish citizen, bought wine.” We have to fight for our right to only be authenticated and authorized.
Thanks for attending my TED talk.
Three Ways to Authenticate
OK, we’ve established that authenticating means producing authentic proof that can be used to authorize us. In a computer system, this is done by first claiming you are a specific user, say JaneDoe, and then authenticating to prove that you should have access to the JaneDoe account. Computers typically give you a challenge that you must respond to and the system checks the validity of the response to authenticate.
Authentication can be done in three ways:
- Something you know. The canonical example is a password.
- Something you have. This can be a card that you blip or a physical key.
- Something you are. This means checking something unique about your body, such as a fingerprint, the pattern of your retina, or the shape of your face. The formal term for this is biometric authentication and this is where pass thoughts come in.
All three forms of authentication have their weaknesses which is why you nowadays often use the combination of two, so called two-factor authentication. That way a weakness in one form can be compensated for with a second.
Weaknesses of Something You Know
Something you know has many weaknesses. Sharing, theft including shoulder surfing, guessability. A password can exist in infinite copies and the computer has no way of knowing if the person producing a password is the rightful owner. People who come up with their own passwords often pick guessable ones.
Weaknesses of Something You Have
Something you have also has the weakness of sharing or theft. But often there only exists one such token, such as the single one in your purse or pocket, and it’s hard to copy it. It ca only be in one physical place at any point in time, such as when you blip a card. That’s different than a password which can be shared over a chat or a phone call.
Weaknesses of Something You Are
Something you are does not have the weakness of sharing or theft. That’s why it’s so attractive as one of the factors in two-factor authentication. It significantly raises the bar for an attacker.
But biometric authentication has its own weaknesses.
First of all, we have yet to see perfect match biometric systems. A password either matches exactly or it doesn’t, but your fingerprint and the scanning of it is not as exact. There could be a person on earth with very a similar fingerprint and the computer may confuse the two. One of the reasons for this fuzziness is user experience. You would stop using your finger to authenticate if it failed 90% of the time because you had a smudge, or didn’t hold your finger just right, or had a scratch. There has to be some tolerance for imperfect biometric matches.
The next weakness is the scanning of this bodily trait of yours. A flat surface reads the grooves of the skin of your fingertip or a camera reads the three-dimensional shape of your face. Those are lossy transfers of data, meaning that the computer is not able to get a flawless read of the flesh, bone, temperature, moisture etc to really authenticate the biometric signal. In that data loss lies the opportunity to use a false fingertip or false face. I’m sure you’ve seen that weakness exploited in numerous Hollywood movies.
Third, you can be forced to use your biometry to unlock a device but no one can force you to state your password.
The final and most scary weakness of biometric authentication is that you can’t change it, or it’s incredibly expensive and intrusive to change it. Your fingerprints and your eyes stay the same throughout your life. Isn’t that great for authentication? It is, until you think about people who need to get new identities. Witnesses who need protection, victims of domestic violence, political refugees, and people who transition to another gender, to name a few. Personal freedom and human rights require the ability to change identity in an orderly fashion. If biometric authentication is forever tied to a person’s old identity, there is no way of getting rid of the link between the old and new. The witness can be found, the refugee tracked down, and the transgender person’s dead name just won’t die. On top of this you have secret agents and law enforcement officers who need to use multiple identities, for instance impersonating a child when trying to trap groomers.
Note that the inability to change a biometric signal is only a problem when it’s used for centralized authentication connected to your identity. Authenticating purely on-device does not have this problem since you can erase the device and there is no hard link to your real, physical identity.
The ones of you who have read Identified will recognize how these challenges play into the plot.
Enter Pass Thoughts
We are now ready for the super cool insight! Pass thoughts are biometric authentication that can change. That’s why I was mind blown when I first read about them.
A pass thought happens when you are presented with a challenge that will produce a response in the form of unique brain waves and those brain waves authenticate you.
Close your eyes and think of an apple.
Your brain just emitted a unique pattern! Was the apple green, red, yellow, or a mix of colors? Was it on a table, in your hand, or still in a tree? Had someone taken a bite of it? I have no way of even enumerating all the possibilities of what your brain’s reaction was. You may be visually impaired and think of an apple as shape, texture, and taste instead of an image.
Importantly, as an attacker, I can’t enumerate the possible challenges. That would be like listing everything you can think of. This is where pass thoughts can allow a person to break the registered link between biometry and identity. They move from thinking of an apple to thinking of a dog to thinking of a specific book to thinking of running. The challenge-response pairs are infinite. And as long as the old challenge is deleted, there is no way to link their old identity with their new one through a pass thought.
Going back to being forced to use your biometry, pass thoughts have a leg up on other biometric schemes there too. Why? Because the one forcing you has to know the challenge, e.g. has to know to show you an apple and not a dog. In a weird way, the challenge works as a password to unlock the right pass thought in your brain. This is why West learning the cottage and snowman scene through Agent Espinoza’s camera glasses was key in my novel.
Pass Thoughts in Real Life
I first came across pass thoughts in 2005 when a research group at Carleton University, Canada published the paper “Pass-thoughts: Authenticating With Our Minds” (pdf). This tells you for how long I took notes before I started writing.
The paper asks a key question for pass thoughts – are people’s brain waves unique enough for authentication? Here’s what they say (citations removed for readability):
There are a number of reasons to believe that there is uniqueness (given genetic and environmental differences) within our brains: certain areas of our brains are developed more depending on our training and experience. For example, string musicians are known to have larger somatosensory cortical areas associated to the fingers than the average person. Also, the alpha frequency (a signal feature in an electroencephalo-graphic (EEG) signal) has been found to have considerable variability between subjects. These results may imply that the signals emitted from our brains are different upon thinking “the same thing”. Thus, it is plausible that if two people think of what they could best describe as the same thing, the brain signals emitted would be distinguishable.
Next key thing is reading the brain waves with enough detail to get a unique signal. This is done through something called a brain–computer interface, or BCI. The data transfer between brain and computer needs to be both robust and secure.
Finally, there’s a challenge in how to allow for some fuzziness (same as with fingerprints) and variability over time in the brain waves. Your thoughts about apples may develop. In my book, Agent Espinoza has chosen a personal memory from his childhood as the thing triggering his pass thought. An early draft featured the backstory with the snowman but it was cut during the many edits. The reason why I chose that scene for Espinoza was my fond memories of the 1982 short movie The Snowman.
Biometry and Pass Thoughts in Fiction
You’ll find many flavors of brain–computer interfaces in fiction. A connector in the back of the skull as in The Matrix, electrodes attached to a shaven skull as with the precogs in Minority Report, or fully wireless as in Identified.
When it comes to full pass thoughts, there’s a cyberpunk anime that’s on my watch list called Psycho-Pass. Here’s Wikipedia’s intro to the plot:
Psycho-Pass is set in a futuristic Japan governed by the Sibyl System, a powerful biomechatronic computer network which endlessly measures the biometrics of Japanese citizens’ brains and mentalities using a “cymatic scan.” The resulting assessment is called a Psycho-Pass, which includes a numeric Crime Coefficient index, revealing the citizen’s criminality potential, and a color-coded Hue, alerting law enforcement to other data, as well as the improvement (clearing) or decline (clouding) of said Psycho-Pass.
I may come back with a review of it!
Currently Reading
I’ve started reading the fifth and currently last book in the Game of Thrones series by George R. R. Martin. The series is actually called A Song of Ice and Fire and the fifth book is titled A Dance with Dragons. Clocking in at 1,100 pages, it’ll take me a while to read.
I brought back about fifteen books from Sweden. Some that you can’t get in the US and several from my late father’s collection, most significantly the autobiography of Jawaharlal Nehru, the first prime minister of India after its independence.