Hacking Printers
Welcome to the March issue of Hacker Chronicles!
I’ve been fretting the fact that I didn’t mention the war in Ukraine in my previous newsletter issue. It was written prior to the February 24th invasion – I typically work on book and movie reviews for a couple of weeks – but it was sent the day after. Let me just say now that I’m appalled by Kremlin’s actions and empathize with Ukrainians who defend their country or flee to save their lives. War in Europe makes me very, very sad.
Below you’ll find my exploration of hacking printers.
Take care!
/John
Writing Update
Identified is still short on reviews on Amazon. If you haven’t already, please consider posting a short review there. Or just rate the book. It helps me a lot. Thank you!
This is where I am in writing the sequel:
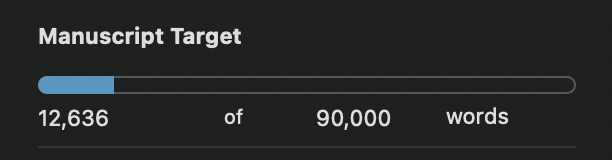
Writing speculative near-future fiction requires me to always think about how things might have changed from today. That’s exciting but can easily turn a two-hour writing session into two hours of online research. Also, this early on most things are fluid. Which points of view should I use? How many plot lines do I want? Who is West after book one?
March Feature: Hacking Printers
Time for the next installment of research I do for fiction writing!
Printers are not as important these days as a couple of decades ago. Today we have tablets and e-readers which can provide a great reading experience. Digital pencils even let you take notes. But kids attending school from home during the pandemic got many of us right back to the familiar sound of printing documents. As for me, I love reading on paper so I print when I need to review a draft.
Modern printers run operating systems and are connected to WiFi. That means complex software with bugs and network access. Or in other words, opportunities for hackers.
Connecting to the Printer
A hacker needs to get a connection to the printer they want to break into. That can be done in three ways – physical access to the printer, local network access which means being on the same WiFi, or remote access, i.e. performing the attack from the internet.
All three can work well in fiction. Physical access has the added benefit of suspense when breaking into a building or the hacker tricking their way in through social engineering.
Fingerprinting Printers
Printers’ WiFi connections allows you to print without a cable from your computer/tablet/smartphone. To facilitate that, printers support the Internet Printing Protocol, or IPP, or something older like Line Printer Daemon, or LPD.
If you’re on the same WiFi network as a printer, you can connect to it through IPP and ask for a bunch of information about what software it’s running and what it is capable of. That’s meant to help with printing, but hackers use it for what they call fingerprinting. Before spending time trying to hack something, they want to know as much as possible about their target device.
A trope in hacker fiction is the know-it-all hacker. A pro who just has it all in their head. No one if capable of that. Information gathering fingerprinting-style is a much better way to have the hacker work the problem and reveal information to the reader. You see that in several scenes in my novel.
Printer Exploitation Toolkit
As hackers develop more and more experience in hacking certain systems, they often share, even publicly. It’s part of the culture and also a way to build fame in the community.
What started as a Master’s thesis project at Ruhr University Bochum (a university I’ve given an invited talk at!) developed into the open source Printer Exploitation Toolkit. It currently has twelve contributors. They also have their own wiki called Printer Security Testing Cheat Sheet.
All this public information means that printers without security updates are likely to be readily hackable just like you see in the movies.
Why Hack Printers?
You may ask yourself why hacking a printer is even interesting for a hacker?
First, modern printers have storage where the latest documents they’ve handled are stored. They can be stolen from that storage. The risks get worse when you consider the fact that printers are often multi functional with copying and scanning capabilities. That printer storage is like a cache of the latest things scanned, copied, or printed.
Second, hacking a printer may give the attacker permanent residence on the local network, something that can be harder to do with computers.
Finally, there’s an angle you hear about much less often. Consider that a hacker with control over a printer can alter documents in order to manipulate or trick humans reading them. Maybe add instructions, change research results, or remove key information. Very useful for fiction.
Spoiler Alert: There’s a spoiler for my novel Identified below.
Printer Watermarking
The opening chapter of Identified has West discover a secret message delivered through printer watermarking based on tiny yellow dots.
The original EFF article on this technology is no longer up but there’s a Wayback Machine copy.
EFF does however have a new mini portal with their collection of research and legal information on printer tracking.
Here’s an example of what such tracking dots look like in blue light, just like West does it in the book: 
The reason at least some laser printers add traceable and practically invisible dot patterns is to help find counterfeiters.
The most recent publicly known case where such dots were used to track a person down was a federal contractor from Augusta, Georgia. In 2017, he was charged with leaking classified material to a news outlet, and they nailed him through the dots.
The fictional leap I made in my novel was Melissa hacking her printer to be able to encode her own messages in such tracker dots.
End spoiler alert
Remarks
As explained above, printers connected to networks are absolutely on hackers’ menu of things to target. They are part of the larger set of digital peripherals you may find in an office or a home. In the set you’ll also find WiFi routers, electronic locks and badging systems, voice assistants, and smart TVs. They all take a step or two away from the tried-and-true personal computer or server hacking we’re all familiar with from movies and books.
At the end of the day, there are computers everywhere in modern things, forming the internet of things, or IoT. A favorite joke among hackers and security professionals is “The S in IoT stands for Security.”
Currently Reading
I’m still reading The Bourne Identity by Robert Ludlum (1980). But I’ve also started reading The Russian Understanding of War: Blurring the Lines between War and Peace by Oscar Jonsson. It’s a rework of his 2019 doctoral thesis, packed with citations every other sentence. It’s great for understanding what’s going on in the world right now.