Fraktal encryption (and an Easter egg)
Welcome to the February issue of Hacker Chronicles!
This issue features a deep dive on “Fraktal encryption” which is a key part of the plot in my hacker thriller Identified. And I will reveal an Easter egg related to the book and Fraktal.
I have a favor to ask: Why not suggest the newsletter to a friend, coworker, or family member! I’m sure you have folks around you who care about hackers and computers in movies. 🙂 Send them this link. And if they’re privacy conscious like me, be sure to tell them that the newsletter free of tracking – no pixels or click IDs. Thank you!
/John
Writing Update
The part of the sequel I’ve been writing lately took me several runs to get through. It’s a segment which features a nice hack, ties in recent developments in the real world of hacking, contains a reveal, and concludes a story arc. That story arc is a sensitive one so I know I’m going to revisit the text several times to get it right. I got teary eyed myself when I wrote it.
I’ve also worked on the story’s theme. It might sound strange to do that late in the game but I’m quite a bit of a “pantser,” i.e. I write by the seat of my pants. Fiction writers are often divided into plotters and pantsers. Plotters make a plan, typically top-down, and have every scene sketched out before they write. Pantsers may just have a beginning and end and then let the story develop as they write. I do some plotting in the beginning but then let the story come naturally. That means the theme may not be crystal clear from the start. Only when I know what happens and how my characters develop can I nail the theme. Then I need to go back and make sure the premise and early plot points are aligned with that theme.
This is where I am right now:
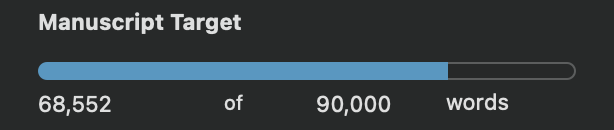
Exactly one year ago, I had only written 8,132 words. That’s 60k words in a year.
February Feature: Fraktal Encryption
Fraktal encryption in my novel is just an alternate, and supposedly Russian spelling of fractal encryption. So let’s start by talking about fractals.
Warning: There are spoilers for my novel Identified below.
My Fascination for Fractals
At either middle or early high school, I got fascinated by fractals. Both the beautiful graphics of the Mandelbrot curve and Julia curve, and the fact that mathematics lay behind it. I hadn’t been taught imaginary numbers yet so I couldn’t go too deep on the math but I wrote a letter to Sweden’s then most well-known professor in this space, Hans Wallin, and he replied with a copy of his latest paper. I still have it, and Prof Wallin is now member of the Royal Swedish Academy of Sciences.
I still have on my bucket list to spend time implementing and visualizing fractals.
 Image from an old Wired article.
Image from an old Wired article.
Fractal Compression
Later, when I was quite a bit along in computer science, I read about fractal compression. The basic idea is that a fractal algorithm can generate a very complex set of data based on a small seed. I remember a quirky image of Benoit Mandelbrot himself compressed and decompressed through fractals. It wasn’t super close to the original but for a human it was clear who it depicted.
Fractal compression is lossy, i.e. you lose some data in the process. Jpeg is another example of lossy compression. Typically when we talk about encryption, any kind of data loss is unacceptable – the decrypted message should be an exact copy of its plaintext original. I briefly touched upon this in my review of Johnny Mnemonic under “Storage Capacity of the Brain.”
But it doesn’t have to be a hard requirement. To pass information between humans, you don’t need digitally identical copies. A jpeg can deliver an image even if some source data was lost.
That idea stuck with me – finding a fractal algorithm that can regenerate data well enough to get a high level message or context across.
The Size of an Encrypted Message
Encryption doesn’t involve compression. In fact, when you account for the decryption key, the total amount of data typically increases a bit when you encrypt. That point can clearly be seen in the most secure encryption algorithm that exists – the one-time pad. The one-time pad is an encryption key the same size as the plaintext message it encrypts, and thus the data doubles.
Here’s an example.
Plaintext message to hide (37 characters):
Transfer $500 to account 8455894-3333
One-time pad (also 37 characters):
0opuhwtui8745uwhwg8ythwgoin9397577573
Cryptotext, using the logical function XOR, and Base64 encoded since some of the encrypted bytes otherwise can't be read as text:
ZB0RGxsREQdJHAIEBVUDB1cGWxobHRkTT1FaDAYBDgEaBAYEAAA=
The superior security of this scheme lies in the fact that there is no way for an attacker to know when they’ve found the right key. Why? Because there are keys that decrypt the cryptotext into every possible 37-character message you can think of.
Transfer $999 to account 8455894-3333
Yup, there’s a key that produces that.
Transfer $500 to account 1111111-1111
Yup, that one too.
Close the bank and go home, you loser
You guessed right, there’s a key that produces that one too.
And also every 37-character misspelled message. So there’s no way for an attacker to get to “Aha! I found the right key!” without knowing what the plaintext message was in the first place.
One-time pads not only use a lot of data, they are also truly one-time. If you reuse the same key for two different 37-character messages, the attack suddenly becomes easy. There’s likely only one key that decrypts both messages into English. All other keys will decrypt into garbage for one or both messages. So the attacker will know when they got the right key and will be able to brute force it.
As mentioned, the size of the keys you have to exchange securely to protect your data with a one-time pad is the same size as the data you want to send. So it’s not a practical scheme.
Smaller Keys and Cryptanalysis
Instead of lengthy one-time pads, practical encryption uses much smaller keys combined with crypto algorithms. That way the data isn’t doubled. But this reduction also introduces a vulnerability. Now a single key cannot decrypt the cryptotext into every possible 37-character message. It’s likely that there is only one key that decrypts the cryptotext into English at all. This means the attacker will know when they’ve found the right key and will be sure what the plaintext message was. This is the basis of cryptanalysis which I mentioned in my review of the hacker movie Sneakers.
Combining It Into Fractal Encryption
The idea of fractal compression and encryption with keys much smaller than the plaintext to protect gave me this idea of fractal encryption many years ago. If the decrypted message doesn’t have to be an exact copy of the original, then fractal compression works and can get the message size down enormously. And if the fractal algorithm generates viable plaintext for many or all seeds, it can make cryptanalysis hard just like with one-time pads.
This idea really should be explored scientifically. But I left academia long ago and just never found a way to publish it. My novel provided a way.
Fractal encryption became the Russian secret crypto algorithm that Agent Pogodina uses to exchange keys with Moscow from her office in Stockholm.
Visualizing Fraktal for the Book
I had it clearly in my head what these fractal-generated messages should look like. And I described them well in the book. But I had on my todo list up until the last stretch to visualize it for the reader. It was one of the last things I did. The book was already proofread at that point.
I first wrote a script that would output random Fraktal text and bake in the two keys. I remember looking for them myself when I saw the proper output for the first time.
Then I had to make the output look pixelated and generated. A graphics program solves that and I used Pixelmator Pro. But when I saw it printed, I worried that the reader would just thing it was poor printing. I still worry about that. It looks compressed and low resolution, exactly like it’s supposed to.
Here’s the source image I produced:
.jpg)
Easter Egg
I promised you an Easter egg related to the book. There are a handful in the book, plus a bunch of pop culture references you may or may not pick up. Only one reader so far has reached out to me after finding one of the Easter eggs.
But the one today is the script I used to generate Fraktal output. It’s been sitting on my website all along: Fraktal generator.
Bonus points if you spot the bug in that code, which I worked around by hand to produce the file in the book.
Now that you know there are Easter eggs actually in the book, I challenge you to find them. I will reveal one of them in my next newsletter issue which is scheduled to land right before … Easter.
Final Thoughts
Imaging something that stuck with me for that long, and finally made its way into a fictional story. Through those years I had the urge to get the idea out somehow. But I had neither the time nor the skills to get it into scientific writing.
I have at least one more such idea and it was part of the original draft for Identified. But it hadn’t become a proper part of the plot. It was just there for my benefit, and those are things that get cut early in editing.
Maybe you have ideas lingering too, that would fit nicely into a great story?
Currently Reading
I’m recently finished reading The Wires of War. Now I’m in the wonderful time of getting to choose my next read. I’ve read a chapter in Tom Clancy’s Red Storm Rising, just to check it out. The size of it is a little daunting. Then I’ve started reading Dark Waters by Lee Vyborny and Don Davis. It’s a non-fiction book on Cold War American submarine NR-1.
I’m still reading The Adventures of Huckleberry Finn for one of our kids. Reading aloud takes a lot of time, especially with so much dialect as in that book.
US law requires me to provide you with a physical address: 6525 Crown Blvd #41471, San Jose, CA 95160